The recent court ruling in the DOJ’s ad tech lawsuit found our advertiser tools and acquisitions don’t harm competition. We disagree with the Court’s ruling on our publi…
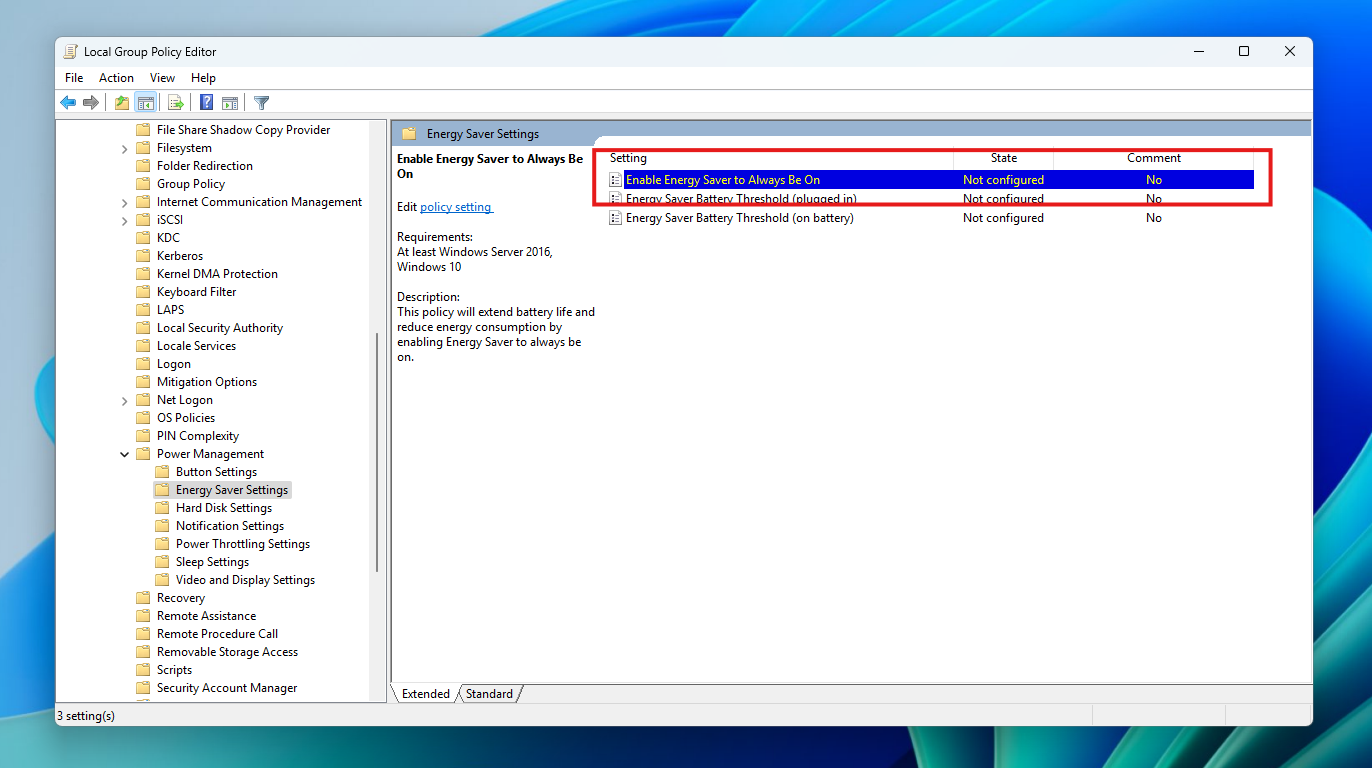
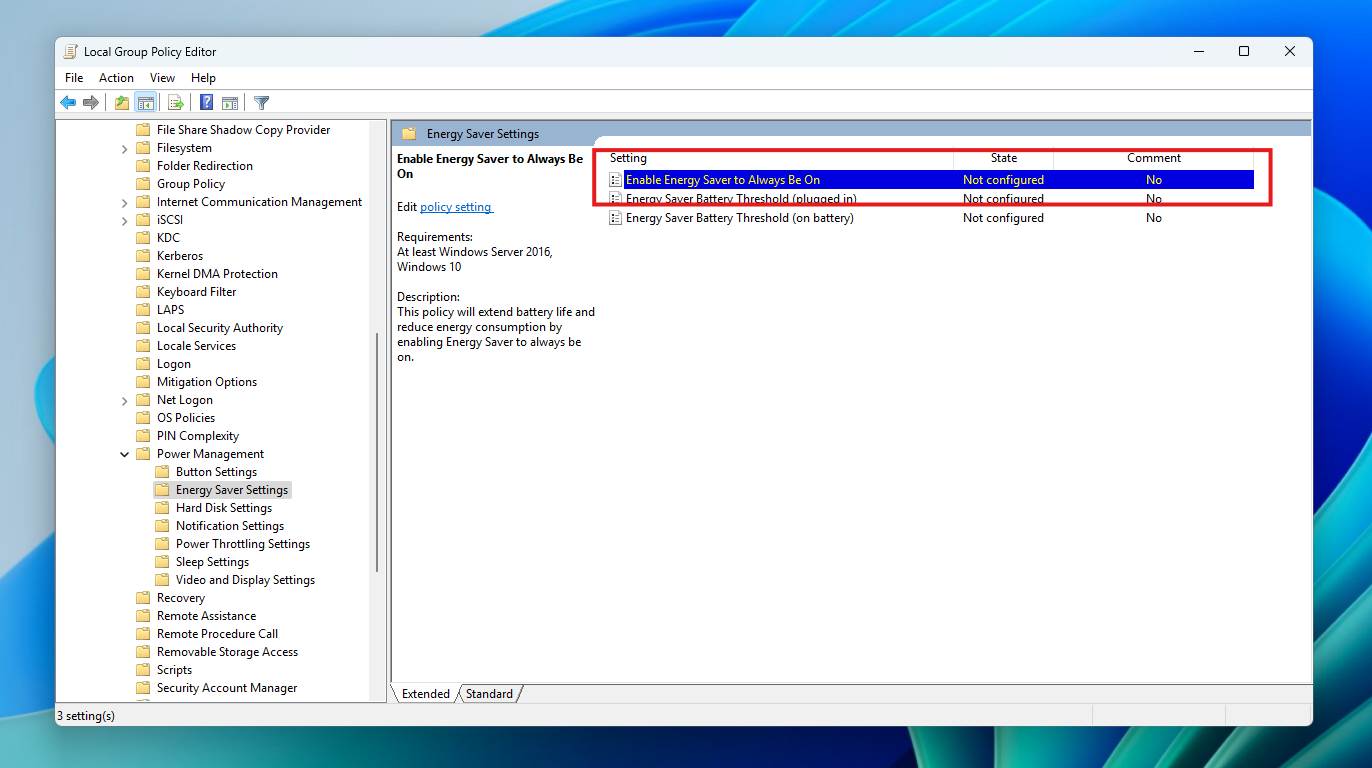
Microsoft Entra ID (formerly Azure Active Directory) is the backbone of modern identity management, enabling secure access to the applications, data, and services your business relies on. As hybrid work and cloud adoption accelerate, Entra ID plays an even more central role — managing authentication, enforcing policy, and connecting users across distributed environments. That prominence […]
A supply-chain attack targets Linux servers with disk-wiping malware hidden in Golang modules published on GitHub. […]
Microsoft has fixed a known issue preventing Windows 11 24H2 feature updates from being delivered via Windows Server Update Services (WSUS) after installing the April 2025 security updates. […]
Google’s newest power purchase agreement (PPA) with Shell is the first time a corporate PPA has extended the lifespan of an offshore wind farm1. This agreement will exte…
Google has released its monthly security updates for Android with fixes for 46 security flaws, including one vulnerability that it said has been exploited in the wild. The vulnerability in question is CVE-2025-27363 (CVSS score: 8.1), a high-severity flaw in the System component that could lead to local code execution without requiring any additional execution […]
A recently disclosed critical security flaw impacting the open-source Langflow platform has been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), citing evidence of active exploitation. The vulnerability, tracked as CVE-2025-3248, carries a CVSS score of 9.8 out of a maximum of 10.0. “Langflow contains a […]
The data-theft extortion group known as Luna Moth, aka Silent Ransom Group, has ramped up callback phishing campaigns in attacks on legal and financial institutions in the United States. […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26200.5581 (KB5055651) to the Dev Channel. Changes in Dev Channel builds and updates are documented in two buckets: new features, improvements, and fixes that are being gradually rolled out for Insiders who have turned on the toggle to get the latest updates as […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.3950 (KB5055653) to the Beta Channel for Windows Insiders on Windows 11, version 24H2. REMINDER: Build 22635.5305 was the last update released to the Beta Channel based on Windows 11, version 23H2. All Insiders in the Beta Channel will be getting upgraded to […]