A proof-of-concept exploit tool has been publicly released for a maximum severity Apache Parquet vulnerability, tracked as CVE-2025-30065, making it easy to find vulnerable servers. […]
Hackers are exploiting an unauthenticated remote code execution (RCE) vulnerability in the Samsung MagicINFO 9 Server to hijack devices and deploy malware. […]
The Legal Aid Agency (LAA), an executive agency of the UK’s Ministry of Justice that oversees billions in legal funding, warned law firms of a security incident and said the attackers might have accessed financial information. […]
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has tagged a Langflow remote code execution vulnerability as actively exploited, urging organizations to apply security updates and mitigations as soon as possible. […]
Google Play helps keep your apps, data, and payments safe, so you can download with confidence.
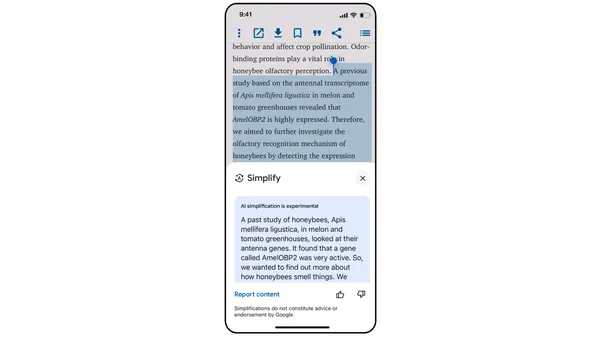
When you’re trying to learn about something new on the web, you might come across content that uses jargon or technical concepts you’re not familiar with. Simplify, a ne…
Threat actors have been observed actively exploiting security flaws in GeoVision end-of-life (EoL) Internet of Things (IoT) devices to corral them into a Mirai botnet for conducting distributed denial-of-service (DDoS) attacks. The activity, first observed by the Akamai Security Intelligence and Response Team (SIRT) in early April 2025, involves the exploitation of two operating system […]
Microsoft is investigating a new Microsoft 365 outage affecting multiple services across North America, including the company’s Teams collaboration platform. […]
Our updated version of Gemini 2.5 Pro has improved capabilities for coding.
You can’t protect what you can’t see. From shadow IT to supplier risk, modern attack surfaces are sprawling fast — and External Attack Surface Management (EASM) is how security teams take back control. Learn from Outpost24 how EASM powers proactive digital risk protection. […]