This year, at Microsoft Build, we introduced new AI tools and capabilities designed to empower every software developer to become an AI developer.
The post New AI innovations that are redefining the future for software companies appeared first on Microsoft Azure Blog.
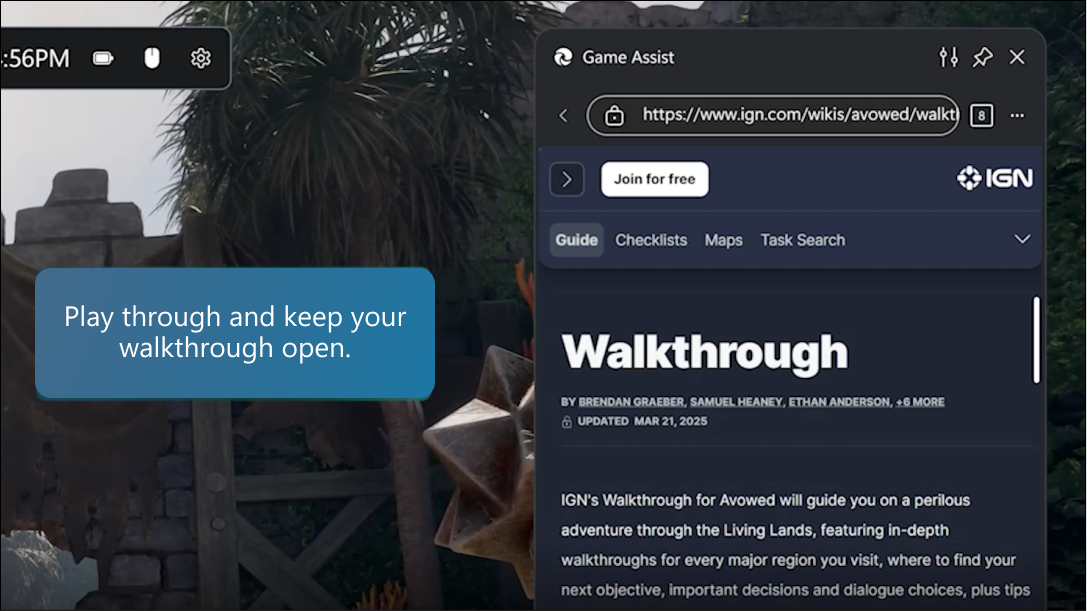
Today, we’re thrilled to announce that Microsoft Edge Game Assist is now available to everyone on Windows 11. We announced the preview of this in-game browser built for PC gaming last November and since then have received valuable feedback to make it
The post Microsoft Edge Game Assist is now available appeared first on Windows Blog.
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 27868 to the Canary Channel.
We are also not planning to release SDKs for 27xxx series builds for the time being.
Changes a
The post Announcing Windows 11 Insider Preview Build 27868 (Canary Channel) appeared first on Windows Blog.
“CyberLock ransomware, developed using PowerShell, primarily focuses on encrypting specific files on the victim’s system,” Cisco Talos researcher Chetan