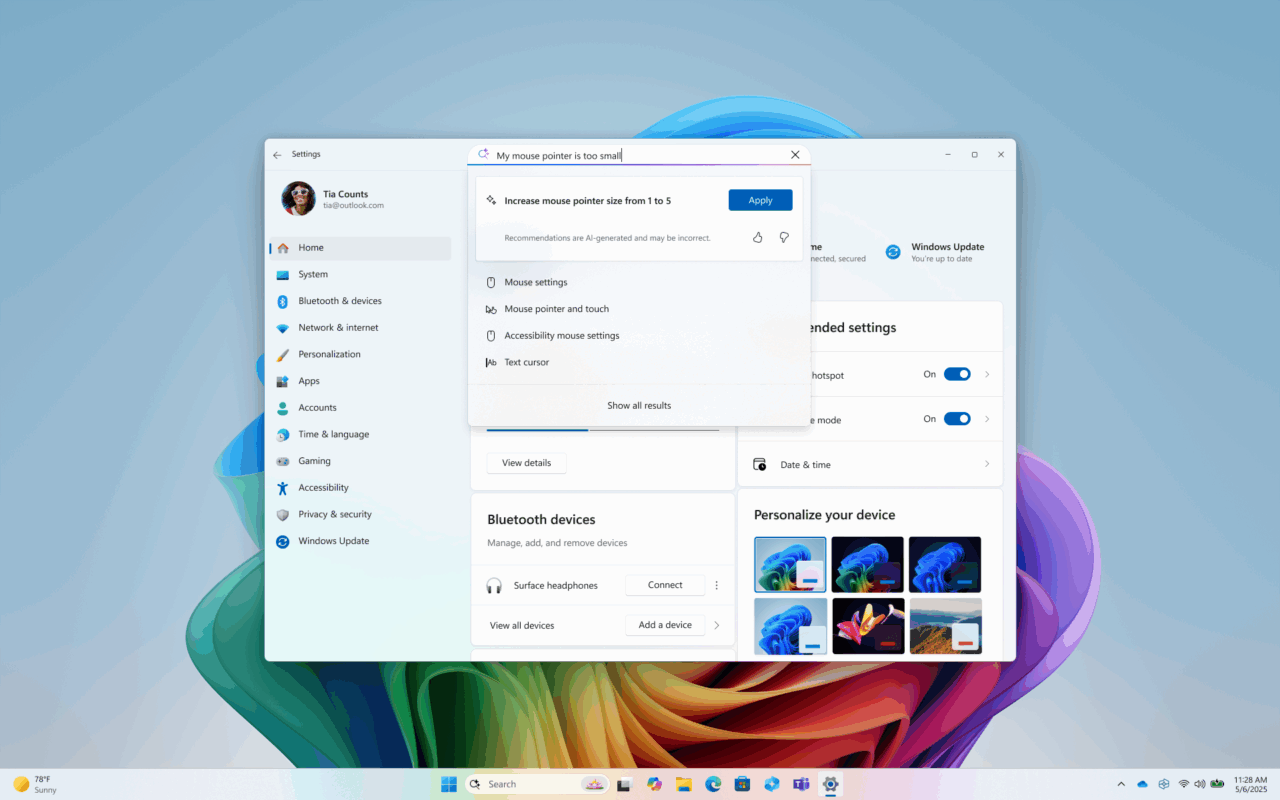
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.3964 (KB5058496) to the Beta Channel for Windows Insiders on Windows 11, version 24H2. REMINDER: Build 22635.5305 was the last update released to the Beta Channel based on Windows 11, version 23H2. All Insiders in the Beta Channel will be getting upgraded to Windows 11, […]
Microsoft has removed an upgrade block that prevented some Safe Exam Browser users from installing the Windows 11 2024 Update due to incompatibility issues. […]
A new campaign employing ClickFix attacks has been spotted targeting both Windows and Linux systems using instructions that make infections on either operating system possible. […]
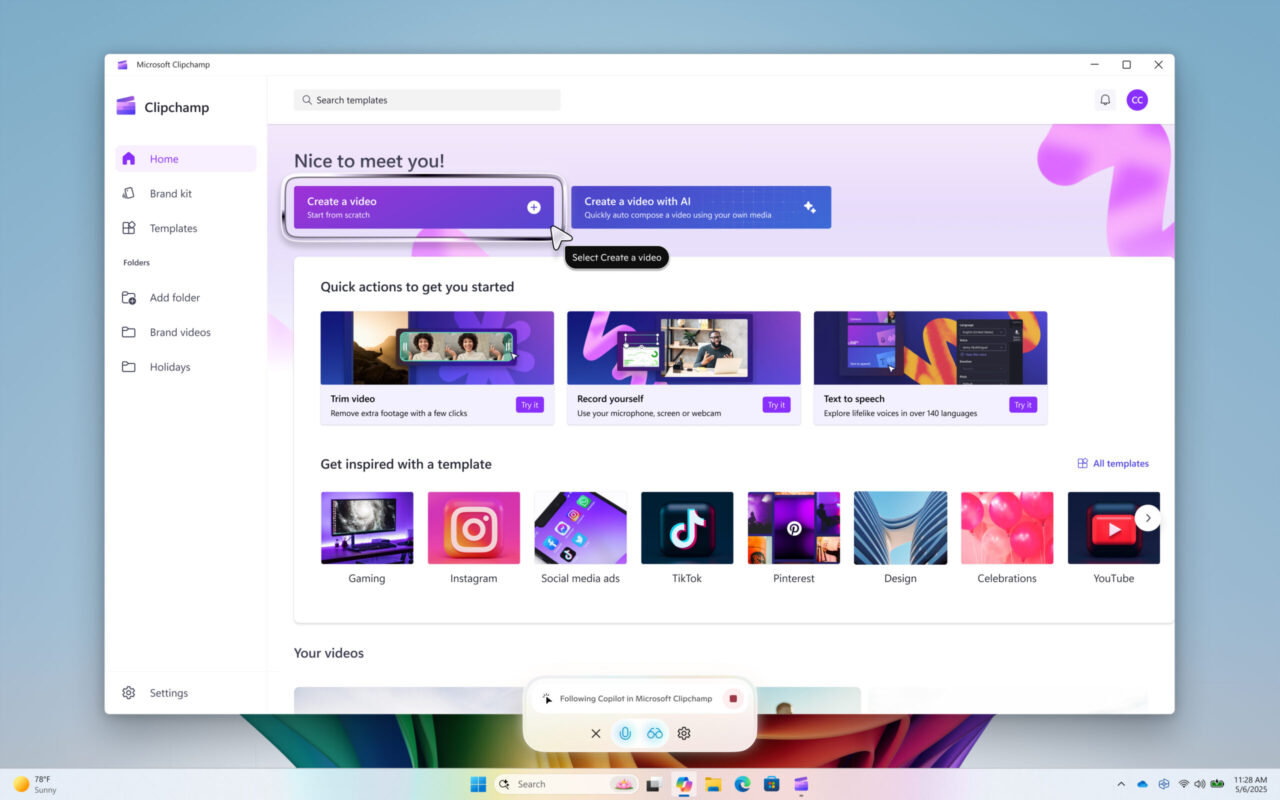
Hello Windows Insiders, we are beginning to roll out an update today for the Microsoft Copilot app on Windows via the Microsoft Store which introduces the following changes and improvements to Copilot Vision on Windows: Highlights: Now when you share a single browser or app window using Copilot Vision, Copilot can guide, navigate, and coach […]
A Türkiye-backed cyberespionage group exploited a zero-day vulnerability to attack Output Messenger users linked to the Kurdish military in Iraq. […]
The AI Futures Fund is a new initiative from Google that invests in and works with startups.
Moldovan authorities have detained a 45-year-old suspect linked to DoppelPaymer ransomware attacks targeting Dutch organizations in 2021. […]
Google has agreed to a $1.375 billion settlement with the state of Texas over a 2022 lawsuit that alleged it had been collecting and using biometric data of millions of Texans without properly acquiring their consent. […]
99% of enterprise users have browser extensions but over half carry high-risk permissions. LayerX’s 2025 report reveals how everyday extensions expose sensitive data, and what security teams must do now. […]
ASUS has released updates to address two security flaws impacting ASUS DriverHub that, if successfully exploited, could enable an attacker to leverage the software in order to achieve remote code execution. DriverHub is a tool that’s designed to automatically detect the motherboard model of a computer and display necessary driver updates for subsequent installation by […]