Today, Microsoft announced the release of Windows 11, version 24H2, the next feature update for its operating system (also known as the Windows 11 2024 Update). […]
Windows Mobile Hotspot now supports 6 GHz connections. This feature is being tested in the latest Windows 11 Insider update (KB5043168). The post Want to use your PC as a mobile hotspot with faster internet? We’ve got some good news appeared first on MSPoweruser.
Today, Pavan Davuluri announced the latest Copilot+ PC innovation and the availability of the Windows 11 2024 Update. We are excited to continue to bring the power of AI and new experiences to Windows 11 and enhance what you can achieve using Copilot+ PCs and Windows 11. In this blog, I’ll share more information on […]
Windows 11 Insider Preview Build 22635.4291 is now out with key updates. With that, Task Manager now gets better dark mode support. The post Windows 11’s KB5043166 update fixes Task Manager which looks weird in dark mode appeared first on MSPoweruser.
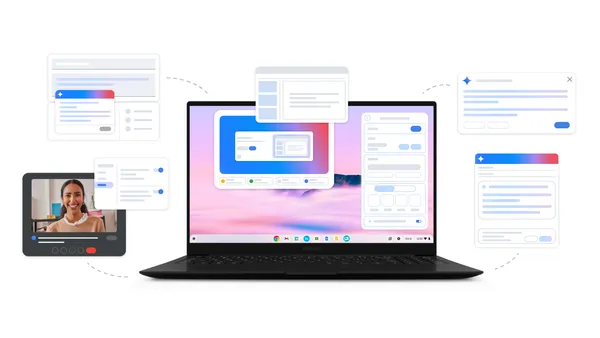
New Chromebook Plus computers with features powered by Google AI to help educators and education leaders.
Today we’re announcing two new Chromebooks, along with new software features that use Google AI to help you get more done.
Originally published by Tata Communications. Written by Rajesh Awasthi, VP & Global Head of Managed Hosting and Cloud Services, Tata Communications. India’s financial sector is undergoing a profound transformation, driven by a confluence of technological advancements, regulatory changes, and evolving consumer expectations. Central to this revolution is cloud computing, increasingly recognized as the key to […]
With AI, content creation has never been easier. Rapidely is based on GPT-4 technology and helps you generate fresh ideas for social media posts. It even has a built-in calendar to manage all your accounts’ posts. In this Rapidely review, I tested the AI tools’ key features to see if it suits your agency, small […]
Whether you’re an individual, influencer, or marketing agency, managing social media takes time and creativity. Fortunately, I tested the best AI for social media management. The following tools and platforms take all the hard work out of managing multiple accounts, composing effective content, and understanding your metrics. After trying every solution possible, here’s my 10 […]
Since its emergence, Generative AI has revolutionized enterprise productivity. GenAI tools enable faster and more effective software development, financial analysis, business planning, and customer engagement. However, this business agility comes with significant risks, particularly the potential for sensitive data leakage. As organizations attempt to balance productivity gains with security