A critical authentication bypass vulnerability has been discovered impacting the WordPress plugin ‘Really Simple Security’ (formerly ‘Really Simple SSL’), including both free and Pro versions. […]
Fake AI image and video generators infect Windows and macOS with the Lumma Stealer and AMOS information-stealing malware, used to steal credentials and cryptocurrency wallets from infected devices. […]
T-Mobile confirms it was hacked in the wave of recently reported telecom breaches conducted by Chinese threat actors to gain access to private communications, call records, and law enforcement information requests. […]
GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and machine learning startup, was targeted in the attack, which has left many wondering about the attacker’s true intentions. […]
Palo Alto Networks has released new indicators of compromise (IoCs) a day after the network security vendor confirmed that a new zero-day vulnerability impacting its PAN-OS firewall management interface has been actively exploited in the wild. To that end, the company said it observed malicious activity originating from below IP addresses and targeting PAN-OS management […]
A threat actor known as BrazenBamboo has exploited an unresolved security flaw in Fortinet’s FortiClient for Windows to extract VPN credentials as part of a modular framework called DEEPDATA. Volexity, which disclosed the findings Friday, said it identified the zero-day exploitation of the credential disclosure vulnerability in July 2024, describing BrazenBamboo as the developer behind […]
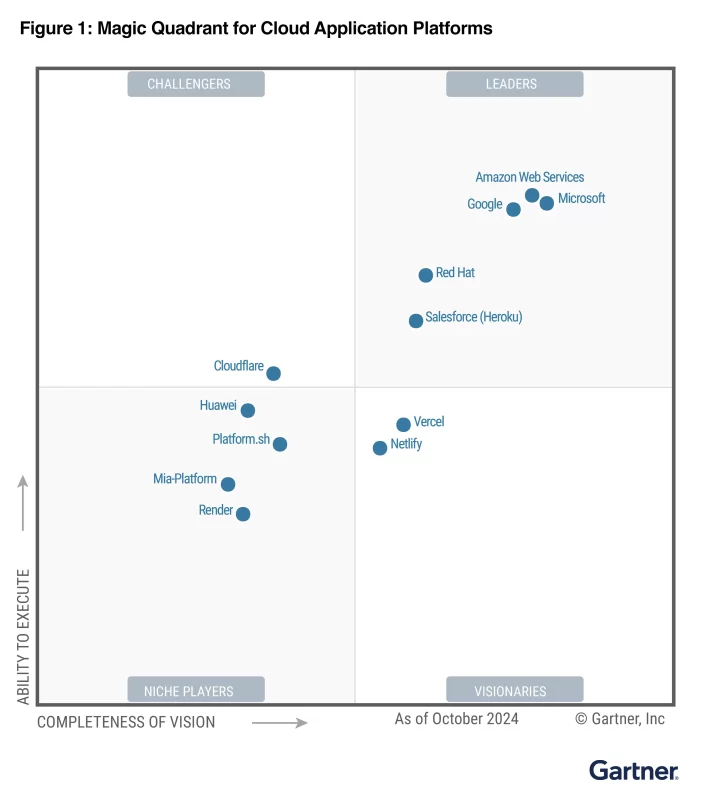
We are excited to share that Microsoft has been recognized as a Leader in the inaugural Gartner® Magic Quadrant™ for Cloud Application Platform. In this report, Gartner placed Microsoft furthest in Completeness of Vision. Microsoft Azure’s comprehensive cloud application platform spans Azure App Service, Azure Container Apps, and Azure Functions to support application modernization and AI […]
Israeli surveillance firm NSO Group reportedly used multiple zero-day exploits, including an unknown one named “Erised,” that leveraged WhatsApp vulnerabilities to deploy Pegasus spyware in zero-click attacks, even after getting sued. […]
A malware botnet is exploiting a zero-day vulnerability in end-of-life GeoVision devices to compromise and recruit them for likely DDoS or cryptomining attacks. […]
On Friday, the U.S. Federal Trade Commission (FTC) reported that the number of consumer complaints about unwanted telemarketing phone calls has dropped over 50% since 2021, continuing a trend that started three years ago. […]