We’ve been investing in XR for more than a decade, and just last month introduced the Android XR platform with our strategic industry partners. Today we signed an agreem…
The RealHome theme and the Easy Real Estate plugins for WordPress are vulnerable to two critical severity flaws that allow unauthenticated users to gain administrative privileges. […]
A security researcher discovered a flaw in Cloudflare’s content delivery network (CDN), which could expose a person’s general location by simply sending them an image on platforms like Signal and Discord. […]
Threat actors on X are exploiting the news around Ross Ulbricht to direct unsuspecting users to a Telegram channel that tricks them into executing PowerShell code that infects them with malware. […]
Cisco has released security updates to patch a ClamAV denial-of-service (DoS) vulnerability, which has proof-of-concept (PoC) exploit code. […]
Learn more about the Android updates from Galaxy Unpacked 2025.
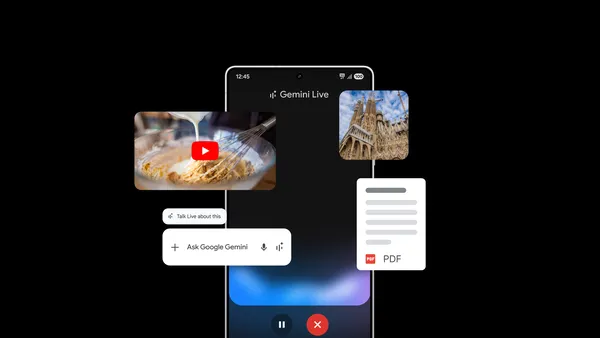
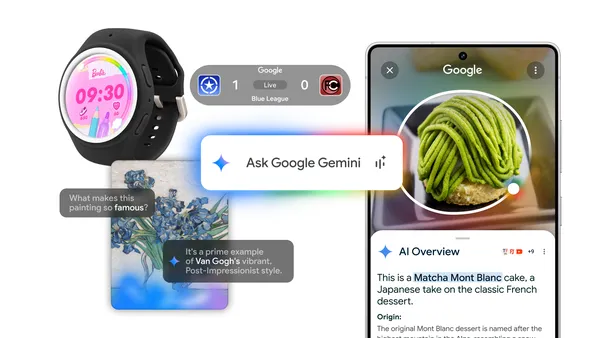
New features for the Gemini app on Android announced at Samsung Galaxy Unpacked.
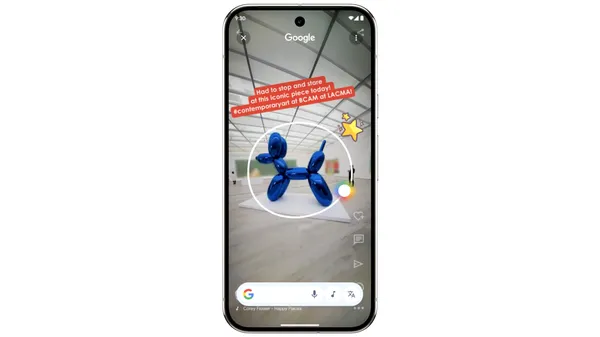
Last year, we introduced Circle to Search to help you easily circle, scribble or tap anything you see on your Android screen, and find information from the web without s…
Learn more about the Google and Android updates announced at Galaxy Unpacked.
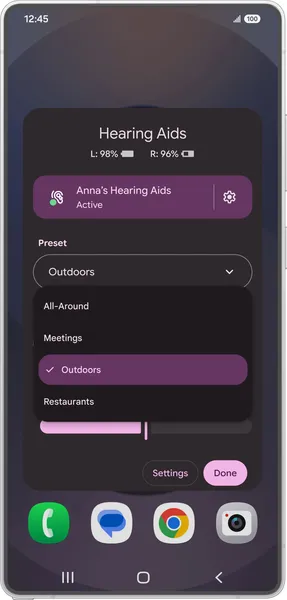
Today we’re rolling out a handful of updates to make Android’s hearing aid and screenreader experiences even more accessible.Starting with the Samsung Galaxy S25, we’re …