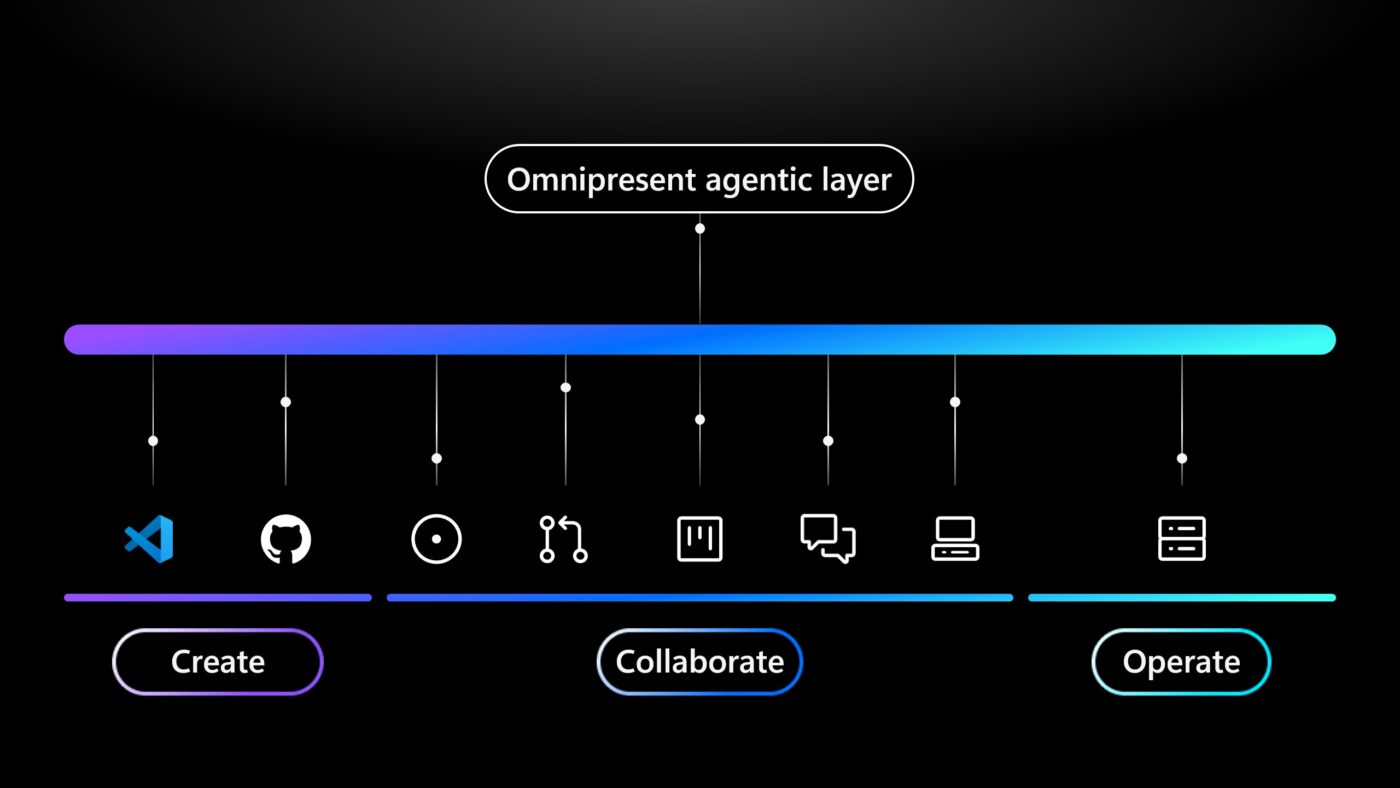
GitHub Copilot has a new coding agent—and it’s ready to join your team. From planning to production, the entire software development lifecycle is being reimagined through intelligent agents—with you at the helm. At Microsoft Build 2025, we’re diving into the seismic shift happening in software development—and unveiling the future we’ll build together. Get started with […]
OpenAI says Operator Agent now uses the o3 model, which means it’s now significantly better at reasoning capabilities. […]
60 packages have been discovered in the NPM index that attempt to collect sensitive host and network data and send it to a Discord webhook controlled by the threat actor. […]
The malware known as Latrodectus has become the latest to embrace the widely-used social engineering technique called ClickFix as a distribution vector. “The ClickFix technique is particularly risky because it allows the malware to execute in memory rather than being written to disk,” Expel said in a report shared with The Hacker News. “This removes […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 27863 to the Canary Channel. We are also not planning to release SDKs for 27xxx series builds for the time being. Changes and Improvements [Post-Quantum Cryptography] As announced this week at the Build conference, we are adding support for post-quantum signature algorithm ML-DSA […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.4161 (KB5058515) to the Beta Channel for Windows Insiders on Windows 11, version 24H2. Changes in Beta Channel builds and updates are documented in two buckets: new features, improvements, and fixes that are being gradually rolled out for Insiders who have turned on […]
At I/O 2025, we shared a major update on our work on Android XR, a new platform for headsets and glasses. We also showed a demo of how Android XR glasses work. Paired wi…
The decentralized exchange Cetus Protocol announced that hackers have stolen $223 million in cryptocurrency and is offering a deal to stop all legal action if the funds are returned. […]
The FBI warned that an extortion gang known as the Silent Ransom Group has been targeting U.S. law firms over the last two years in callback phishing and social engineering attacks. […]
Originally published by CXO REvolutionaries. Written by Ben Corll, CISO in Residence, Zscaler. Cybersecurity and privacy are foundational concerns for most organizations. While these concepts are often discussed together, they are distinct yet interconnected disciplines with unique objectives. In an era dominated by data-driven decision-making, digital primacy, and evolving threats, cybersecurity and […]