DogWifTools has disclosed on its official Discord channel that its software has been compromised by a supply chain attack that impacted its Windows client, infecting users with malware. […]
AI is moving closer to the edge, and Copilot+ PCs are leading the way. With the availability of cloud hosted DeepSeek R1 available on Azure AI Foundry, we’re bringing NPU-optimized versions of DeepSeek-R1 directly to Copilot+ PCs, starting with Qualcomm Snapdragon X first, followed by Intel Core Ultra 200V and others. The first release, DeepSeek-R1-Distill-Qwen-1.5B […]
AI holds immense possibilities for not just cybersecurity — but economic and national security.
In 2024, we continued to invest in more ways to protect our community and fight bad actors, so billions of people can trust the apps they download from Google Play and m…
Three vulnerabilities discovered in the open-source PHP package Voyager for managing Laravel applications could be used for remote code execution attacks. […]
AI Usage Statement: This research was done with Claude Desktop, Web Search, Web Document Fetch, and Sequential Thinking. Claude wrote the report, under the direction of Kurt Seifried and validated by ChatGPT. Methodology, templates, and raw conversation are available upon request. January 2025 marked a fundamental shift in our understanding of AI development. DeepSeek, a […]
Microsoft is investigating an ongoing outage preventing users and admins from accessing some Microsoft 365 services and the admin center. […]
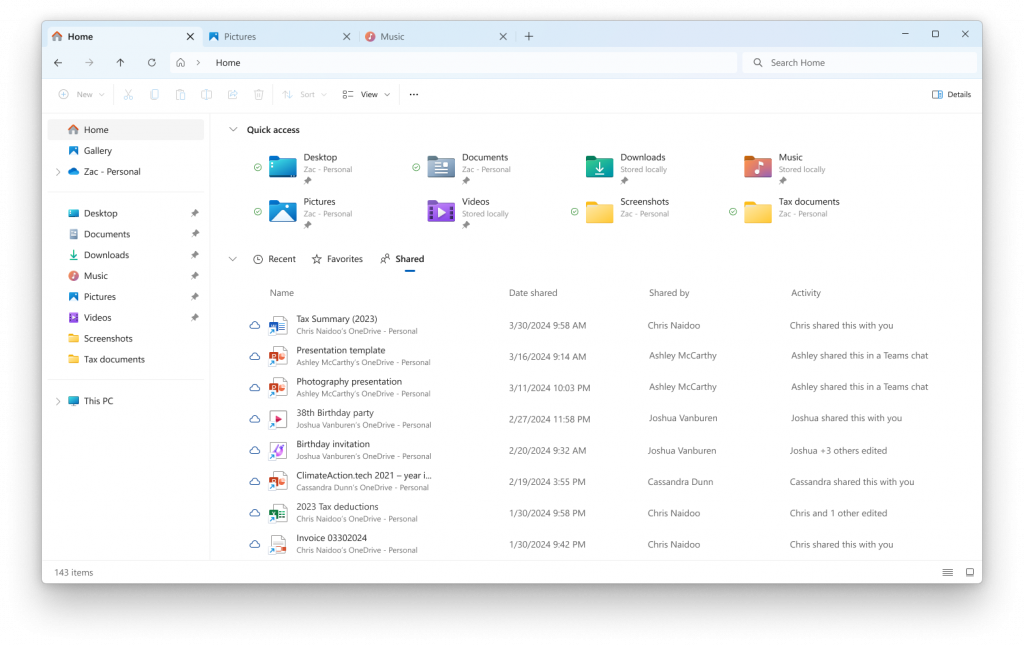
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 27783 to the Canary Channel. We are also not planning to release SDKs for 27xxx series builds for the time being. What’s new with Build 27783 Shared Content in File Explorer Home File Explorer will now provide you with quick access to files […]
The FBI has seized the domains for the infamous Cracked.io and Nulled.to hacking forums, which are known for their focus on cybercrime, password theft, cracking, and credential stuffing attacks. […]
The North Korean threat actor known as the Lazarus Group has been observed leveraging a “web-based administrative platform” to oversee its command-and-control (C2) infrastructure, giving the adversary the ability to centrally supervise all aspects of their campaigns. “Each C2 server hosted a web-based administrative platform, built with a React application and a Node.js API,” SecurityScorecard’s