North Korean state actor ‘Kimsuky’ (aka ‘Emerald Sleet’ or ‘Velvet Chollima’) has been observed using a new tactic inspired from the now widespread ClickFix campaigns. […]
Android Enterprise provides a high-quality suite of built-in accessibility tools that address the needs of employees with vision, hearing and mobility disabilities.
Ivanti has released security updates for Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), and Ivanti Secure Access Client (ISAC) to address multiple vulnerabilities, including three critical severity problems. […]
A subgroup within the infamous Russian state-sponsored hacking group known as Sandworm has been attributed to a multi-year initial access operation dubbed BadPilot that stretched across the globe. “This subgroup has conducted globally diverse compromises of Internet-facing infrastructure to enable Seashell Blizzard to persist on high-value targets and support tailored network operations,” the
A subgroup of the Russian state-sponsored hacking group APT44, also known as ‘Seashell Blizzard’ and ‘Sandworm’, has been targeting critical organizations and governments in a multi-year campaign dubbed ‘BadPilot.’ […]
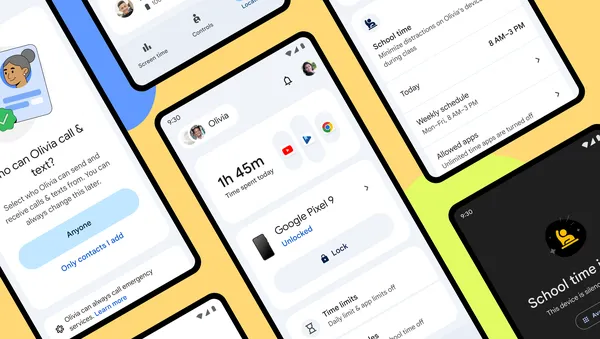
We’re bringing built-in protections to more kids and teens, and equipping parents with additional tools to support safer experiences.
Google Family Link is introducing new features that help families foster healthy digital habits.
Cloud-based RDP Remote Desktop Protocol solutions offer a centralized dashboard to manage user access, security policies, and monitor usage from one location. Learn more from TruGrid about how their SecureRDP platform provides a secure, scalable, and cost-efficient alternative to VPN-based RDP implementations. […]
Written by the CSA New Jersey Chapter:Stanley Mierzwa, Ph.D.; CISSP, Director, Center for Cybersecurity, Transformational Learning and External Affairs, Kean University Eliot Perez, Director, Information Technology, Township of Bedminster, New Jersey Remember Y2K, in the context of the worry for many technologists and engineers working in the computer field? For many, it may feel like […]
Cybersecurity researchers have discovered a bypass for a now-patched security vulnerability in the NVIDIA Container Toolkit that could be exploited to break out of a container’s isolation protections and gain complete access to the underlying host. The new vulnerability is being tracked as CVE-2025-23359 (CVSS score: 8.3). It affects the following versions – NVIDIA Container […]