Google has announced the rollout of artificial intelligence (AI)-powered scam detection features to secure Android device users and their personal information. “These features specifically target conversational scams, which can often appear initially harmless before evolving into harmful situations,” Google said. “And more phone calling scammers are using spoofing techniques to hide their real
Check out Waze’s latest driving experience with Chaka Khan
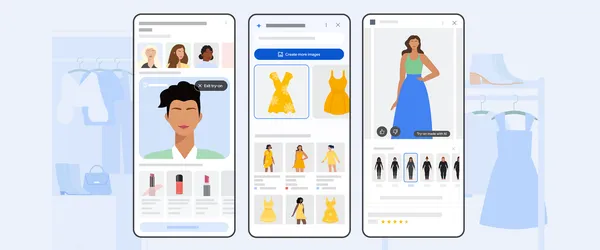
Learn more about Google Shopping’s new AI tools, like image generation for shopping, new AR beauty features and more.
The threat actor known as Lotus Panda has been observed targeting government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with updated versions of a known backdoor called Sagerunex. “Lotus Blossom has been using the Sagerunex backdoor since at least 2016 and is increasingly employing long-term persistence command shells and […]
The rapid adoption of cloud services, SaaS applications, and the shift to remote work have fundamentally reshaped how enterprises operate. These technological advances have created a world of opportunity but also brought about complexities that pose significant security threats. At the core of these vulnerabilities lies Identity—the gateway to enterprise security and the number one […]
Originally published by Vanta. SaaS security requires constantly monitoring and preparing to mitigate the latest industry threats and vulnerabilities. According to the 2024 State of SaaS Security Report, 58% of organizations experienced a SaaS security incident in the past year despite having high confidence levels in their existing security programs. Today, SaaS applications are […]
Cybersecurity researchers are alerting of an ongoing malicious campaign targeting the Go ecosystem with typosquatted modules that are designed to deploy loader malware on Linux and Apple macOS systems. “The threat actor has published at least seven packages impersonating widely used Go libraries, including one (github[.]com/shallowmulti/hypert) that appears to target financial-sector developers
Scammers are impersonating the BianLian ransomware gang in fake ransom notes sent to US companies via snail mail through the United States Postal Service. […]
What was the last thing you did with a generative AI app? Create a cat-unicorn coloring book for your niece? Summarize that 42-page brief a colleague sent you? For me, it was using Microsoft Copilot to help my 9th grader with a history study session—I know more than you can believe about Mesopotamia. Whatever it […]
New research has uncovered further links between the Black Basta and Cactus ransomware gangs, with members of both groups utilizing the same social engineering attacks and the BackConnect proxy malware for post-exploitation access to corporate networks. […]