Cisco has released security updates to patch a ClamAV denial-of-service (DoS) vulnerability, which has proof-of-concept (PoC) exploit code. […]
Category Archives: Security
Auto Added by WPeMatico
The hacker who breached education tech giant PowerSchool claimed in an extortion demand that they stole the personal data of 62.4 million students and 9.5 million teachers. […]
American business services giant and government contractor Conduent confirmed today that a recent outage resulted from what it described as a “cyber security incident.” […]
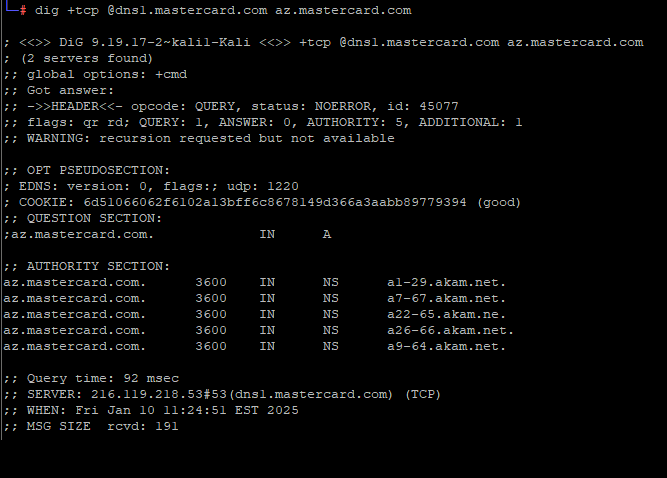
The payment card giant MasterCard just fixed a glaring error in its domain name server settings that could have allowed anyone to intercept or divert Internet traffic for the company by registering an unused domain name. The misconfiguration persisted for nearly five years until a security researcher spent $300 to register the domain and prevent […]
South Korean VPN provider IPany was breached in a supply chain attack by the “PlushDaemon” China-aligned hacking group, who compromised the company’s VPN installer to deploy the custom ‘SlowStepper’ malware. […]
Creating a custom password-exclusion list can help prevent employees from using passwords that are likely to be guessed. Learn from Specops Software on using AI to generate password dictionary for securing your organization’s credentials. […]
On the first day of Pwn2Own Automotive 2025, security researchers exploited 16 unique zero-days and collected $382,750 in cash awards. […]
The largest distributed denial-of-service (DDoS) attack to date peaked at 5.6 terabits per second and came from a Mirai-based botnet with 13,000 compromised devices. […]
Hackers are once again abusing Google ads to spread malware, using a fake Homebrew website to infect Macs and Linux devices with an infostealer that steals credentials, browser data, and cryptocurrency wallets. […]
A high-severity vulnerability in the 7-Zip file archiver allows attackers to bypass the Mark of the Web (MotW) Windows security feature and execute code on users’ computers when extracting malicious files from nested archives. […]