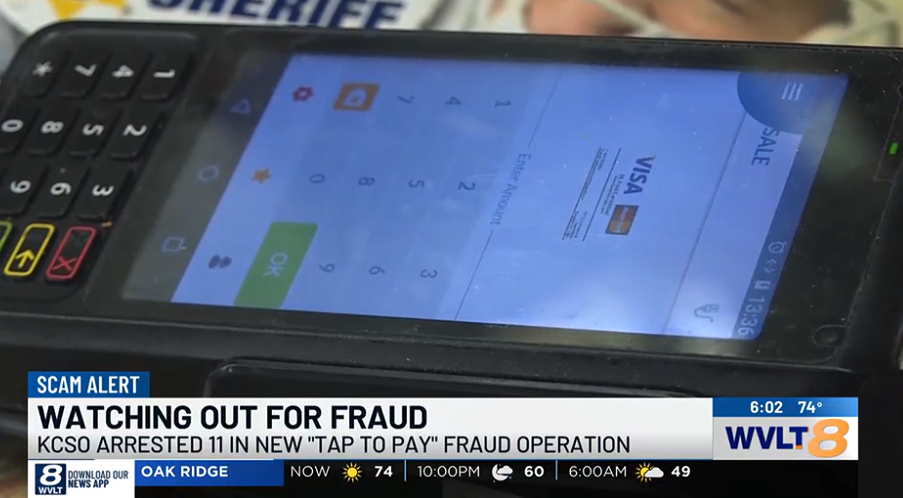
Authorities in at least two U.S. states last week independently announced arrests of Chinese nationals accused of perpetrating a novel form of tap-to-pay fraud using mobile devices. Details released by authorities so far indicate the mobile wallets being used by the scammers were created through online phishing scams, and that the accused were relying on […]
Category Archives: Security
Auto Added by WPeMatico
A new phishing campaign is targeting SEO professionals with malicious Semrush Google Ads that aim to steal their Google account credentials. […]
Microsoft is investigating an Exchange Online bug causing anti-spam systems to mistakenly quarantine some users’ emails. […]
The U.S. Department of Treasury announced today that it has removed sanctions against the Tornado Cash cryptocurrency mixer, which North Korean Lazarus hackers used to launder hundreds of millions stolen in multiple crypto heists. […]
Valve has removed a game titled ‘Sniper: Phantom’s Resolution’ from the Steam store following multiple user reports that indicated its demo installer actually infected their systems with information stealing malware. […]
Veeam has patched a critical remote code execution vulnerability tracked as CVE-2025-23120 in its Backup & Replication software that impacts domain-joined installations. […]
CISA has warned U.S. federal agencies to secure their networks against attacks exploiting a high-severity vulnerability in NAKIVO’s Backup & Replication software. […]
Two malicious VSCode Marketplace extensions were found deploying in-development ransomware from a remote server, exposing critical gaps in Microsoft’s review process. […]
Attackers have started targeting Cisco Smart Licensing Utility (CSLU) instances unpatched against a vulnerability exposing a built-in backdoor admin account. […]
Security researchers have linked a new backdoor dubbed Betruger, deployed in several recent ransomware attacks, to an affiliate of the RansomHub operation. […]