SAP has released out-of-band emergency updates for NetWeaver to fix an actively exploited remote code execution (RCE) vulnerability used to hijack servers. […]
Category Archives: Security
Auto Added by WPeMatico
SAP has released out-of-band emergency NetWeaver updates to fix a suspected remote code execution (RCE) zero-day flaw actively exploited to hijack servers. […]
The FBI has asked the public for information on Chinese Salt Typhoon hackers behind widespread breaches of telecommunications providers in the United States and worldwide. […]
Russian threat actors have been abusing legitimate OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of employees of organizations related to Ukraine and human rights. […]
In a recent espionage campaign, the infamous North Korean threat group Lazarus targeted multiple organizations in the software, IT, finance, and telecommunications sectors in South Korea. […]
A ransomware attack in January at Frederick Health Medical Group, a major healthcare provider in Maryland, has led to a data breach affecting nearly one million patients. […]
The Interlock ransomware gang has claimed the cyberattack on DaVita kidney dialysis firm and leaked data allegedly stolen from the organization. […]
Yale New Haven Health (YNHHS) is warning that threat actors stole the personal data of 5.5 million patients in a cyberattack earlier this month. […]
A significant security gap in Linux runtime security caused by the ‘io_uring’ interface allows rootkits to operate undetected on systems while bypassing advanced Enterprise security software. […]
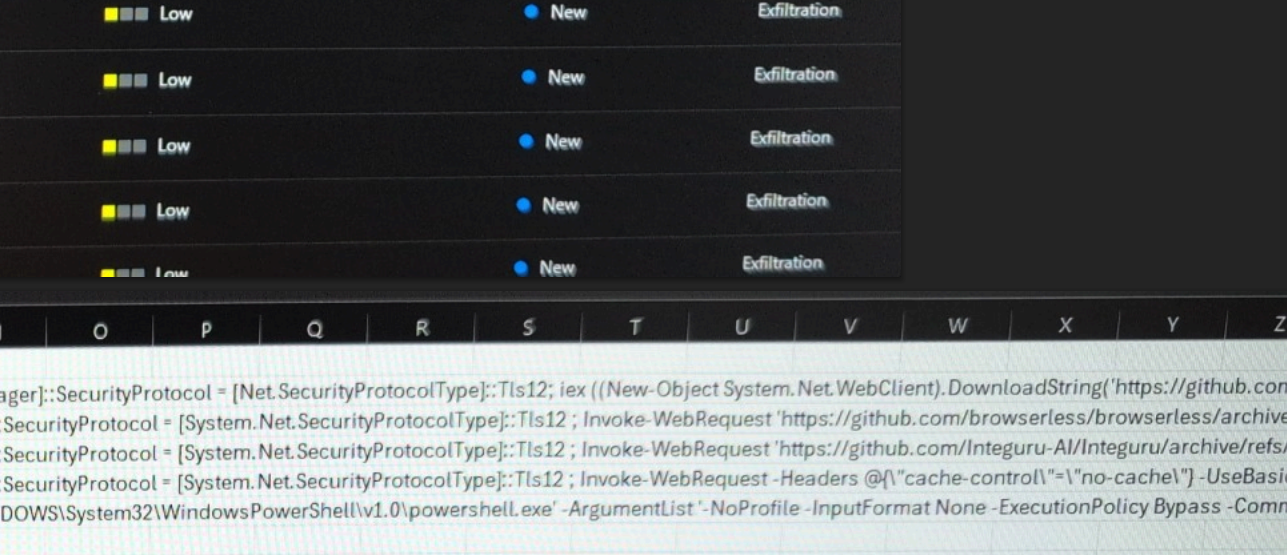
A Little Sunshine, async-ip-rotator, Browserless, Daniel J. Berulis, Department of Government Efficiency, Department of Health and Human Services, DOGE, Ge0rg3, Github, Integuru, Krebs, Labor Department, Marko Elez, National Labor Relations Board, News, Politico, Security, The Coming Storm, The Wall Street Journal
DOGE Worker’s Code Supports NLRB Whistleblower
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency’s sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one […]