Background check service National Public Data confirms that hackers breached its systems after threat actors leaked a stolen database with millions of social security numbers and other sensitive personal information. […]
Category Archives: Security
Auto Added by WPeMatico
CISA warned on Thursday that attackers are exploiting a recently patched critical vulnerability in SolarWinds’ Web Help Desk solution for customer support. […]
A common yet overlooked type of weak password are keyboard walk patterns. Learn more from Specops Software on finding and blocking keyboard walk passwords in your organization. […]
A Little Sunshine, Atlas Data Privacy Corp., Data Breaches, fbi, HaveIBeenPwned.com, InfraGard, Instant Checkmate, Jerico Pictures, Krebs, National Criminal Data LLC, National Public Data breach, News, PeopleConnect, recordscheck.net, Sal Verini, Salvatore Verini, Security, Shadowglade LLC, SXUL, The Coming Storm, Trinity Entertainment, Troy Hunt, TruthFinder, Twisted History LLC, USDoD, VX-Underground
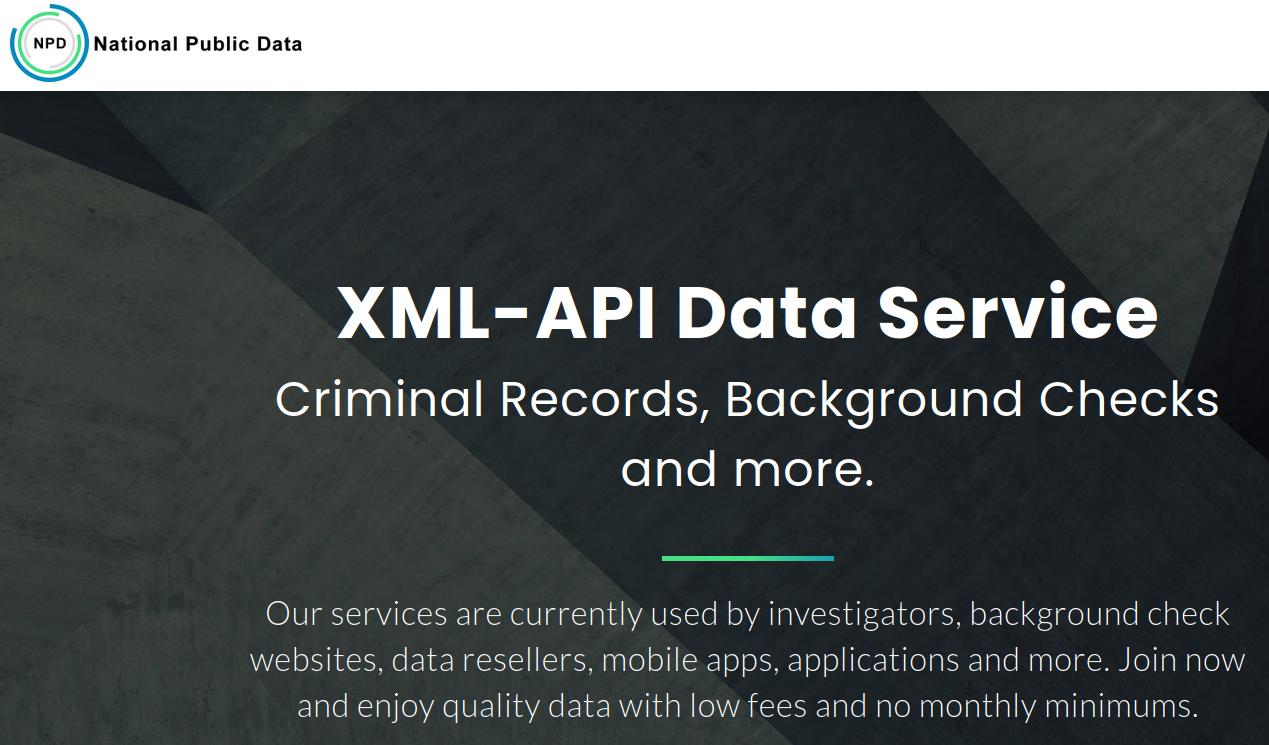
NationalPublicData.com Hack Exposes a Nation’s Data
A great many readers this month reported receiving alerts that their Social Security Number, name, address and other personal information were exposed in a breach at a little-known but aptly-named consumer data broker called NationalPublicData.com. This post examines what we know about a breach that has exposed hundreds of millions of consumer records. We’ll also […]
RansomHub ransomware operators have been spotted deploying new malware to disable Endpoint Detection and Response (EDR) security software in Bring Your Own Vulnerable Driver (BYOVD) attacks […]
Microsoft has disabled a fix for a BitLocker security feature bypass vulnerability due to firmware incompatibility issues that were causing patched Windows devices to go into BitLocker recovery mode. […]
Georgy Kavzharadze, a 27-year-old Russian national, has been sentenced to 40 months in prison for selling login credentials for over 300,000 accounts on Slilpp, the largest online marketplace of stolen logins, until its seizure in June 2021. […]
Microsoft warned customers this Tuesday to patch a critical TCP/IP remote code execution (RCE) vulnerability with an increased likelihood of exploitation that impacts all Windows systems with IPv6 enabled. […]
Microsoft warned customers this Tuesday to patch a critical TCP/IP remote code execution (RCE) vulnerability with an increased likelihood of exploitation that impacts all Windows systems with IPv6 enabled. […]
Multiple high-profile open-source projects, including those from Google, Microsoft, AWS, and Red Hat, were found to leak GitHub authentication tokens through GitHub Actions artifacts in CI/CD workflows. […]