The Data Protection Commission (DPC) in Ireland has fined Meta Platforms Ireland Limited (MPIL) €91 million ($100 million) for storing in plaintext passwords of hundreds of millions of users. […]
Category Archives: Security
Auto Added by WPeMatico
The U.S. Department of Justice unsealed an indictment charging three Iranian hackers with a “hack-and-leak” campaign that aimed to influence the 2024 U.S. presidential election. […]
Microsoft has announced security and privacy upgrades to its AI-powered Windows Recall feature, which now can be removed and has stronger default protection for user data and tighter access controls. […]
Microsoft warns that ransomware threat actor Storm-0501 has recently switched tactics and now targets hybrid cloud environments, expanding its strategy to compromise all victim assets. […]
Progress Software warned customers to patch multiple critical and high-severity vulnerabilities in its WhatsUp Gold network monitoring tool as soon as possible. […]
Cybersecurity is more than just a technical requirement for any organization; it’s essential for survival. Like the delicate balance of a coral reef, our digital ecosystems must adapt and strengthen to withstand evolving threats. Corals face threats like bleaching from temperature changes, pollution, and disease. Similarly, digital ecosystems battle sophisticated cyberattacks, ransomware, and evolving malware. […]
Under certain conditions, attackers can chain a set of vulnerabilities in multiple components of the CUPS open-source printing system to execute arbitrary code remotely on vulnerable machines. […]
A new variant of the RomCom malware called SnipBot, has been used in attacks that pivot on the network to steal data from compromised systems. […]
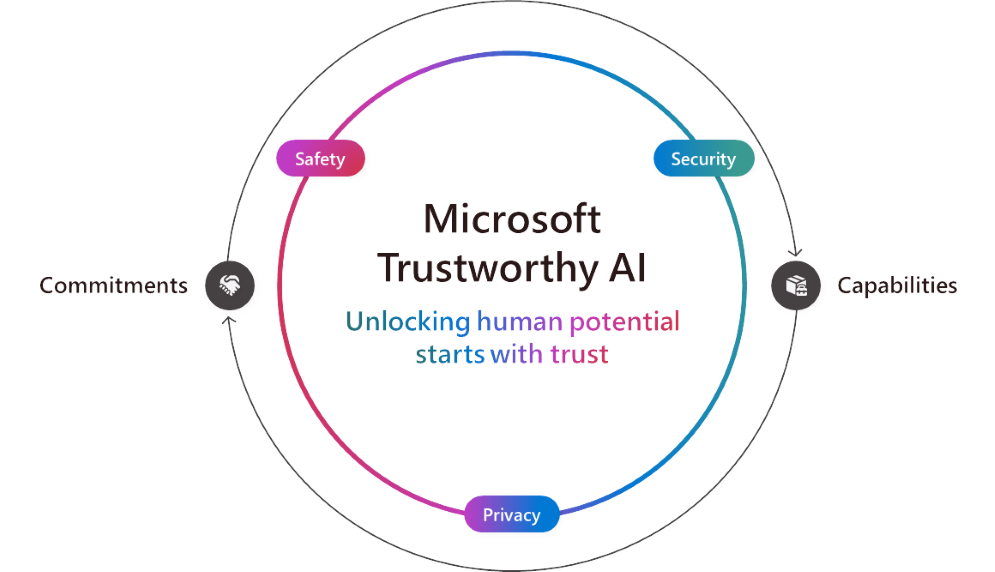
As AI advances, we all have a role to play to unlock AI’s positive impact for organizations and communities around the world. That’s why we’re focused on helping customers use and build AI that is trustworthy, meaning AI that is secure, safe and private. At Microsoft, we have commitments to ensure Trustworthy AI and are building industry-leading supporting technology. Our […]
A group of security researchers discovered critical flaws in Kia’s dealer portal that could let hackers locate and steal millions of Kia cars made after 2013 using just the targeted vehicle’s license plate. […]