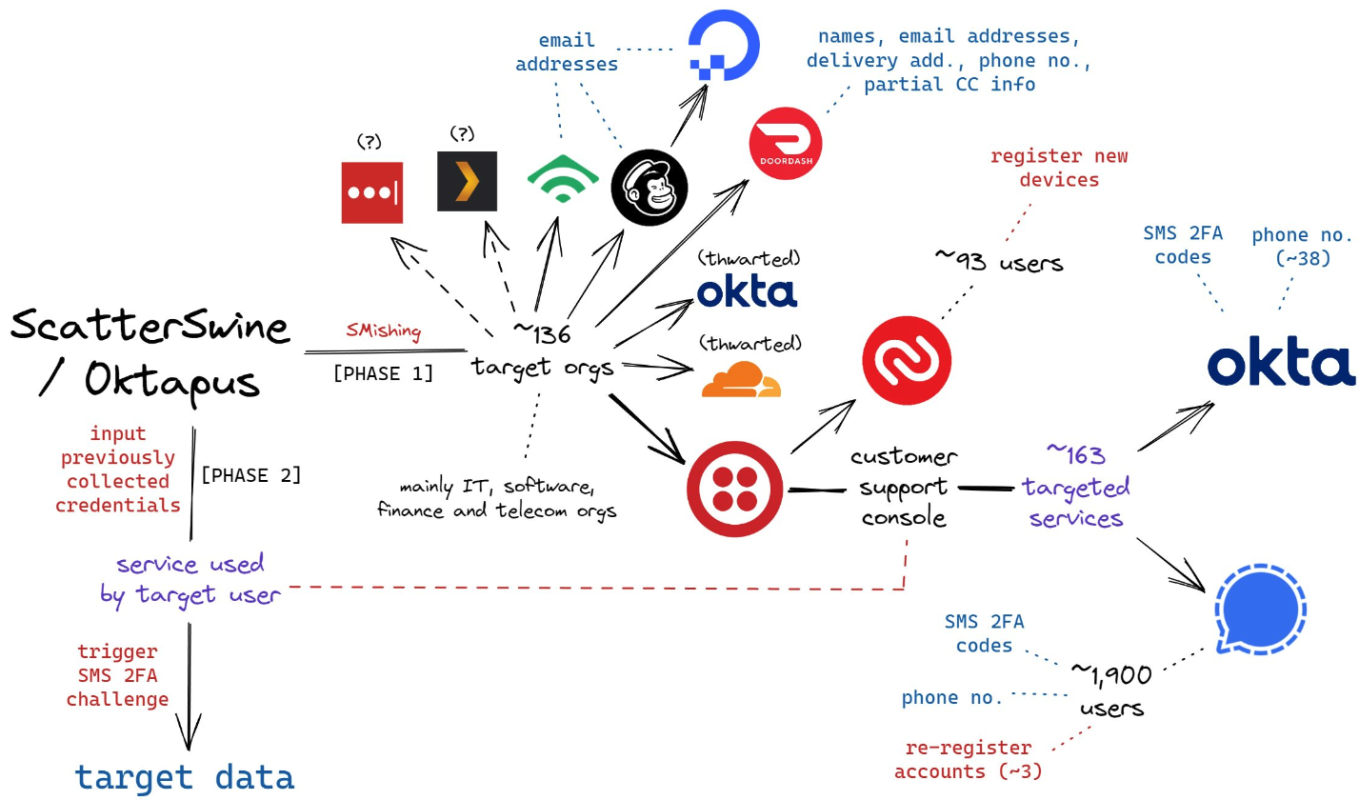
Federal prosecutors in Los Angeles this week unsealed criminal charges against five men alleged to be members of a hacking group responsible for dozens of cyber intrusions at major U.S. technology companies between 2021 and 2023, including LastPass, MailChimp, Okta, T-Mobile and Twilio. A visual depiction of the attacks by the SMS phishing group known […]
Category Archives: Security
Auto Added by WPeMatico
A new Linux backdoor called ‘WolfsBane’ has been discovered, believed to be a port of Windows malware used by the Chinese ‘Gelsemium’ hacking group. […]
Hackers have already compromised thousands of Palo Alto Networks firewalls in attacks exploiting two recently patched zero-day vulnerability vulnerabilities. […]
The BianLian ransomware operation has shifted its tactics, becoming primarily a data theft extortion group, according to an updated advisory from the U.S. Cybersecurity & Infrastructure Security Agency, the FBI, and the Australian Cyber Security Centre. […]
Microsoft has seized 240 domains used by customers of ONNX, a phishing-as-a-service (PhaaS) platform, to target companies and individuals across the United States and worldwide since at least 2017. […]
A design flaw in the Fortinet VPN server’s logging mechanism can be leveraged to conceal the successful verification of credentials during a brute-force attack without tipping off defenders of compromised logins. […]
As users are flocking to BlueSky from social media platforms like X/Twitter, so are threat actors. BleepingComputer has spotted cryptocurrency scams popping up on BlueSky just as the decentralized microblogging service surpassed 20 million users this week. […]
A data breach at an unnamed French hospital exposed the medical records of 750,000 patients after a threat actor gained access to its electronic patient record system. […]
Finastra has confirmed it warned customers of a cybersecurity incident after a threat actor began selling allegedly stolen data on a hacking forum. […]
MITRE has shared this year’s top 25 list of the most common and dangerous software weaknesses behind more than 31,000 vulnerabilities disclosed between June 2023 and June 2024. […]