The Interlock ransomware gang has claimed the cyberattack on DaVita kidney dialysis firm and leaked data allegedly stolen from the organization. […]
Category Archives: Security
Auto Added by WPeMatico
Yale New Haven Health (YNHHS) is warning that threat actors stole the personal data of 5.5 million patients in a cyberattack earlier this month. […]
A significant security gap in Linux runtime security caused by the ‘io_uring’ interface allows rootkits to operate undetected on systems while bypassing advanced Enterprise security software. […]
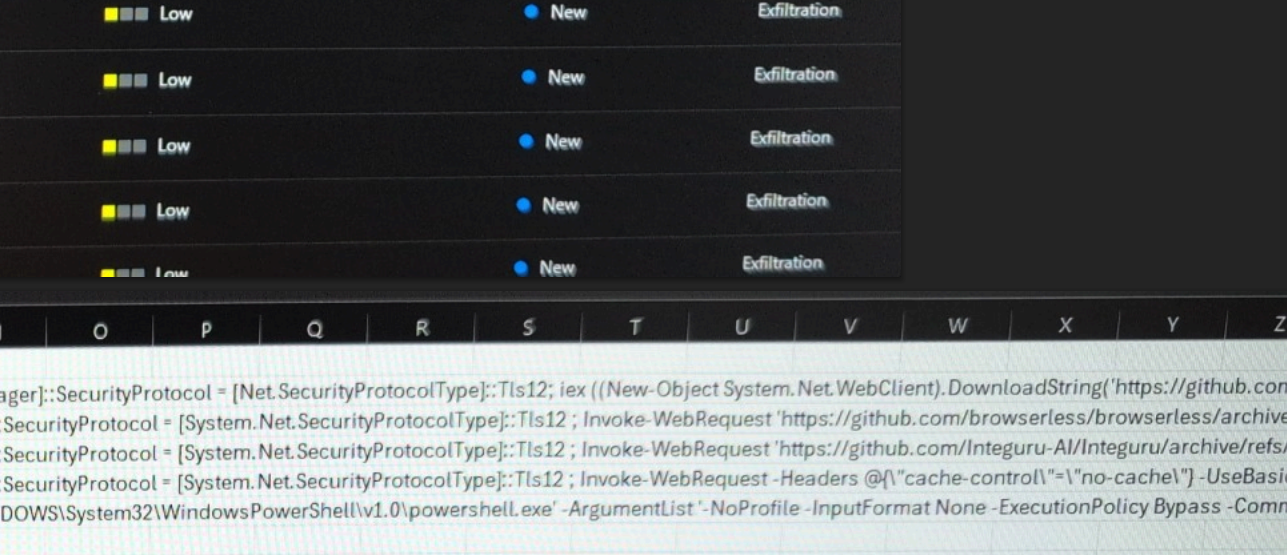
A Little Sunshine, async-ip-rotator, Browserless, Daniel J. Berulis, Department of Government Efficiency, Department of Health and Human Services, DOGE, Ge0rg3, Github, Integuru, Krebs, Labor Department, Marko Elez, National Labor Relations Board, News, Politico, Security, The Coming Storm, The Wall Street Journal
DOGE Worker’s Code Supports NLRB Whistleblower
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency’s sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one […]
A new Android malware has been discovered hidden inside trojanized versions of the Alpine Quest mapping app, which is reportedly used by Russian soldiers as part of war zone operational planning. […]
WhatsApp has introduced a new Advanced Chat Privacy feature to protect sensitive information exchanged in private chats and group conversations. […]
Blue Shield of California disclosed it suffered a data breach after exposing protected health information of 4.7 million members to Google’s analytics and advertisement platforms. […]
The FBI says cybercriminals have stolen a record $16,6 billion in 2024, marking an increase in losses of over 33% compared to the previous year. […]
ASUS has released security updates to address CVE-2024-54085, a maximum severity flaw that could allow attackers to hijack and potentially brick servers. […]
Phishing attacks now evade email filters, proxies, and MFA — making every attack feel like a zero-day. This article from Push Security breaks down why detection is failing and how real-time, in-browser analysis can help turn the tide. […]