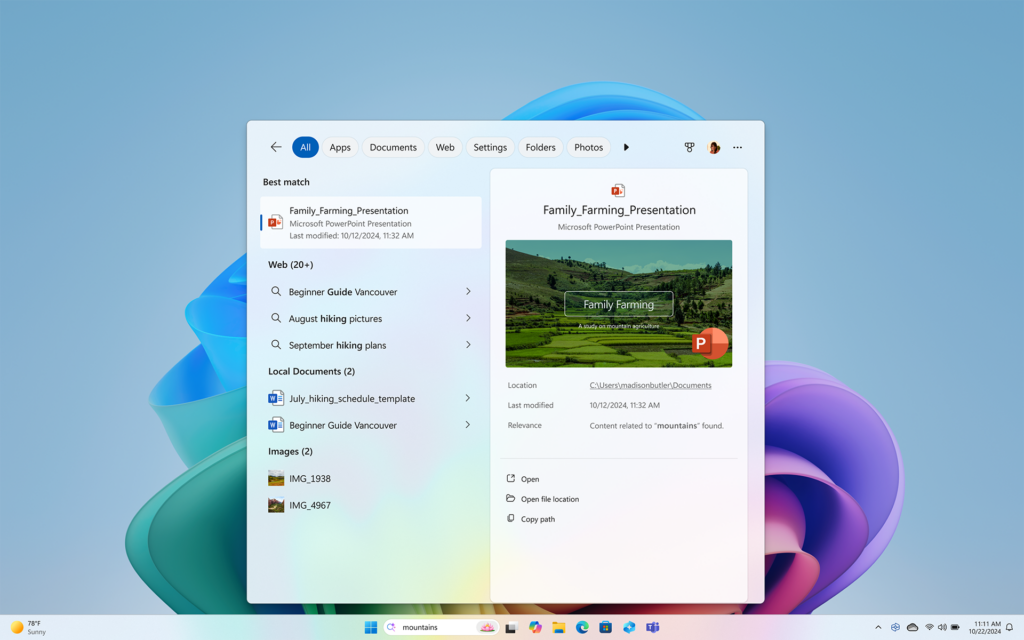
Windows has always been the place where computing innovation happens first. This was the case when we introduced Copilot+ PCs last May – the fastest, most intelligent and most secure Windows PCs ever built, and continues today with the general availability (GA) of exclusive AI experiences like Recall (preview), Click To Do (preview) and improved […]
Category Archives: News
Go behind the scenes on the development of Google Cloud WAN, now available to external customers for the first time.
British retailer giant Marks & Spencer (M&S) has suspended online orders while working to recover from a recently disclosed cyberattack. […]
African mobile giant MTN Group announced that a cybersecurity incident has compromised the personal information of some of its subscribers in certain countries. […]
A recent Windows security update that creates an ‘inetpub’ folder has introduced a new weakness allowing attackers to prevent the installation of future updates. […]
Baltimore City Public Schools notified tens of thousands of employees and students of a data breach following an incident in February when unknown attackers hacked into its network. […]
North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute malware during the fake hiring process. “In this new campaign, the threat actor group is using three front companies in the cryptocurrency consulting industry—BlockNovas LLC (blocknovas[.] com), Angeloper Agency (angeloper[.]com), and SoftGlide LLC (softglide[.]co)—to spread
The Cloud Controls Matrix (CCM) is a framework of controls that are essential for cloud computing security. It is created and updated by CSA and aligned to CSA best practices. You can use CCM to systematically assess and guide the security of any cloud implementation. CCM also provides guidance on which actors within the cloud […]
SAP has released out-of-band emergency updates for NetWeaver to fix an actively exploited remote code execution (RCE) vulnerability used to hijack servers. […]
SAP has released out-of-band emergency NetWeaver updates to fix a suspected remote code execution (RCE) zero-day flaw actively exploited to hijack servers. […]