A hacker targets other hackers, gamers, and researchers with exploits, bots, and game cheats in source code hosted on GitHub that contain hidden backdoors to give the threat actor remote access to infected devices. […]
Category Archives: News
Hewlett Packard Enterprise (HPE) has released security updates to address as many as eight vulnerabilities in its StoreOnce data backup and deduplication solution that could result in an authentication bypass and remote code execution.
“These vulnerabilities could be remotely exploited to allow remote code execution, disclosure of information, server-side request forgery, authentication bypass,
“These vulnerabilities could be remotely exploited to allow remote code execution, disclosure of information, server-side request forgery, authentication bypass,
We’ve pulled together the top 25 announcements at Microsoft Build 2025 across the Azure business—spanning Azure AI Foundry, Azure infrastructure, Azure app platform, Azure databases and Microsoft Fabric, and our GitHub family.
The post All the Azure news you don’t want to miss from Microsoft Build 2025 appeared first on Microsoft Azure Blog.
OpenAI’s next big foundational model is GPT-5, and the AI startup is hoping that the model will compete a little more with rivals. […]
ChatGPT’s memory feature is now better and capable of referencing past conversations for free accounts. […]
Hewlett Packard Enterprise (HPE) has issued a security bulletin to warn about eight vulnerabilities impacting StoreOnce, its disk-based backup and deduplication solution. […]
A recently disclosed data breach at Coinbase has been linked to India-based customer support representatives from outsourcing firm TaskUs, who threat actors bribed to steal data from the crypto exchange. […]
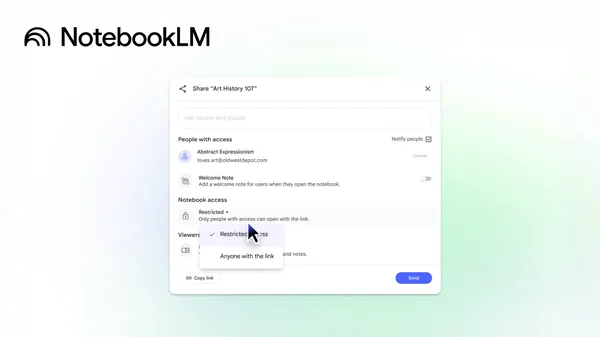
 Many people who use NotebookLM already share their notebooks with classmates, coworkers, students and friends. Today, we’re making sharing and curation easier — with pub…
Many people who use NotebookLM already share their notebooks with classmates, coworkers, students and friends. Today, we’re making sharing and curation easier — with pub… Gemini 2.5 has new capabilities in AI-powered audio dialog and generation.
Gemini 2.5 has new capabilities in AI-powered audio dialog and generation.Microsoft is testing a dedicated page in Windows Settings for quick machine recovery, which will provide users with additional configuration options. […]