The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday revealed that Commvault is monitoring cyber threat activity targeting applications hosted in their Microsoft Azure cloud environment. “Threat actors may have accessed client secrets for Commvault’s (Metallic) Microsoft 365 (M365) backup software-as-a-service (SaaS) solution, hosted in Azure,” the agency said. “This
Category Archives: News
Cybersecurity researchers have discovered an indirect prompt injection flaw in GitLab’s artificial intelligence (AI) assistant Duo that could have allowed attackers to steal source code and inject untrusted HTML into its responses, which could then be used to direct victims to malicious websites. GitLab Duo is an artificial intelligence (AI)-powered coding assistant that enables users […]
Today, OpenAI rival Anthropic announced Claude 4 models, which are significantly better than Claude 3 in benchmarks, but we’re left disappointed with the same 200,000 context window limit. […]
A Little Sunshine, Aleksandr Stepanov, Artem Aleksandrovich Kalinkin, DanaBot, DCIS, Defense Criminal Investigative Service, ESET, fbi, Flashpoint, Google, Intel 471, JimmBee, Krebs, Lumen, Lumma Stealer, Maffiozi, Microsoft, Ne'er-Do-Well News, News, Onix, Paypal, proofpoint, Russia's War on Ukraine, Security, team cyrmu, U.S. Department of Justice, Zscaler
Oops: DanaBot Malware Devs Infected Their Own PCs
The U.S. government today unsealed criminal charges against 16 individuals accused of operating and selling DanaBot, a prolific strain of information-stealing malware that has been sold on Russian cybercrime forums since 2018. The FBI says a newer version of DanaBot was used for espionage, and that many of the defendants exposed their real-life identities after […]
The U.S. government has indicted Russian national Rustam Rafailevich Gallyamov, the leader of the Qakbot botnet malware operation that compromised over 700,000 computers and enabled ransomware attacks. […]
At this week’s I/O, we announced our very latest products, tools and research designed to make AI even more helpful with Gemini. The latest episode of the Google AI: Rel…
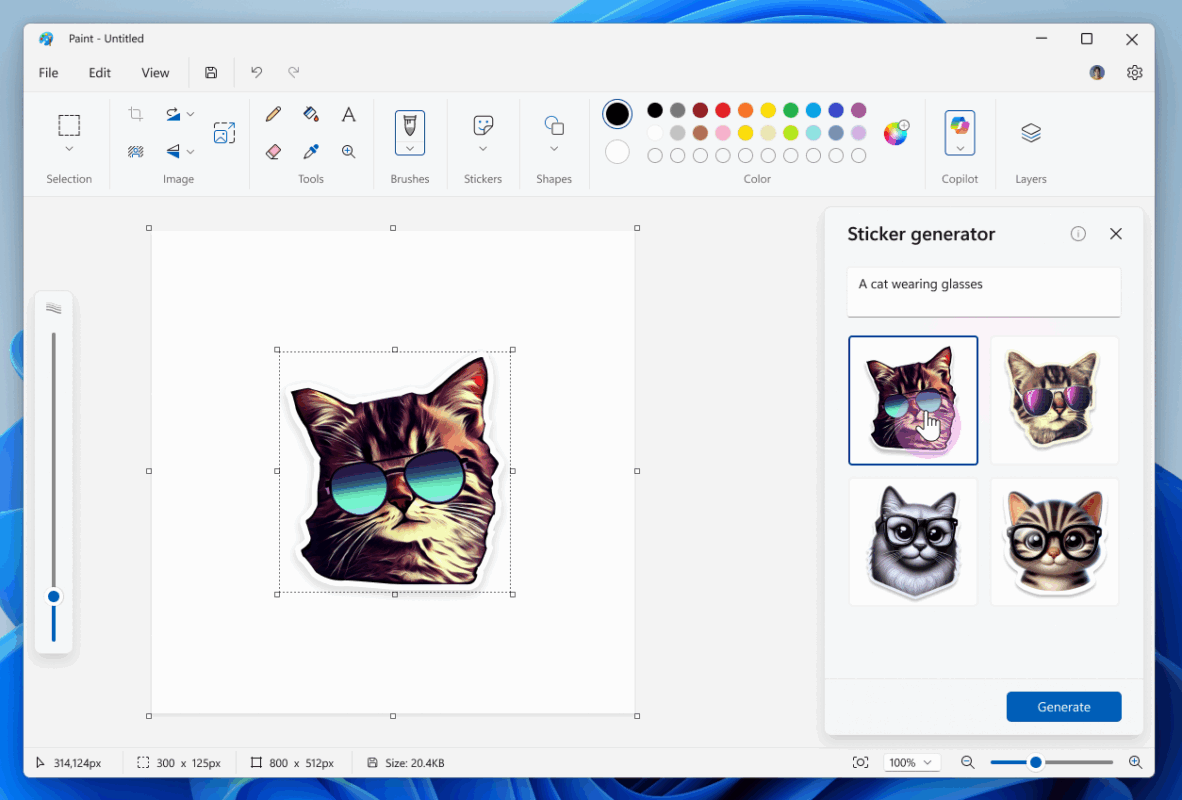
Hello Windows Insiders, today we are beginning to roll out updates to Paint, Snipping Tool, and Notepad to Windows Insiders in the Canary and Dev Channels on Windows 11. Paint (version 11.2504.451.0) This update brings three exciting enhancements to elevate your creative experience. First, we’re introducing sticker generator, a new AI-powered feature that lets you […]
Cybercriminal campaigns are using fake Ledger apps to target macOS users and their digital assets by deploying malware that attempts to steal seed phrases that protect access to digital cryptocurrency wallets. […]
Take this quiz about Google I/O 2025 to see how well you know what we announced this year at I/O.
Police arrested 270 suspects following an international law enforcement action codenamed ‘Operation RapTor’ that targeted dark web vendors and customers from ten countries. […]