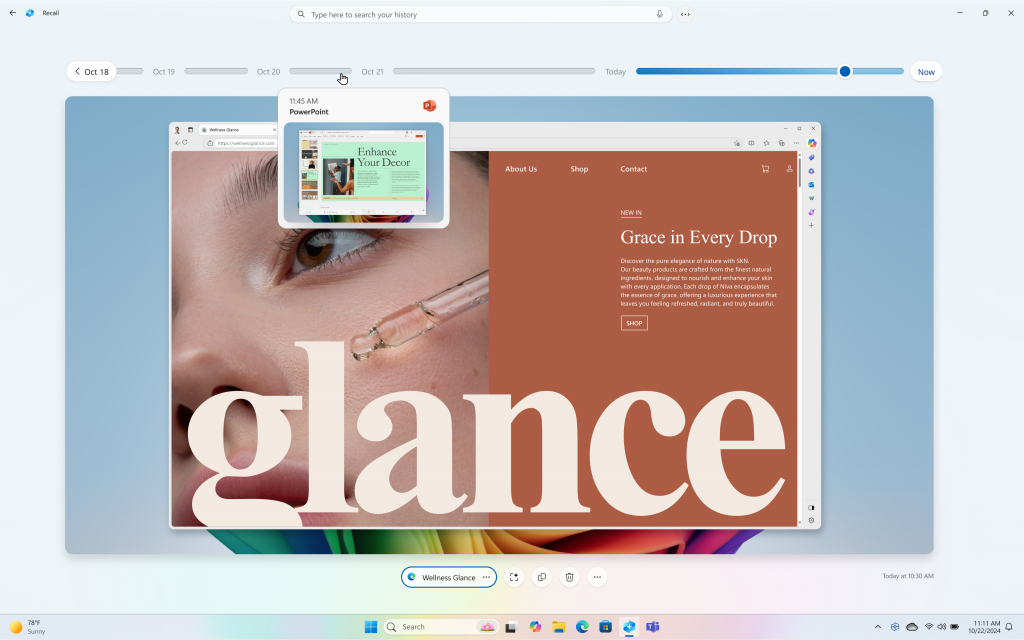
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.2510 (KB5048780) to the Dev Channel. With this update, we are previewing new experiences for AMD and Intel-powered Copilot+ PCs including Recall and more and expanding Click to Do (Preview) beyond Recall in Windows. Join the Dev Channel on your Copilot+ PC Here […]
Category Archives: News
Today we’re announcing the 22 recipients in the 2024 cycle of the exploreCSR program.
Google’s AI model, Gemini, was launched with Gemini 1.0 one year ago. Take this pop quiz to see how well you’ve been paying attention!
The Termite ransomware gang has officially claimed responsibility for the November breach of software as a service (SaaS) provider Blue Yonder. […]
A new zero-day vulnerability has been discovered that allows attackers to capture NTLM credentials by simply tricking the target into viewing a malicious file in Windows Explorer. […]
Exec posts, Microsoft News, News, Recent News
One of my favorite examples of how Copilot is transforming work is Copilot in Excel. You start with a high-level prompt, and Copilot uses advanced reasoning capabilities to build out a full plan. Just like how Excel improved population-scale number-sense, we think Copilot in Excel with Python will improve analysis-sense for the world. Try it for yourself.
The post One of my favorite examples of how Copilot is transforming work is Copilot in Excel. You start with a high-level prompt, and Copilot uses advanced reasoning capabilities to build out a full plan. Just like how Excel improved population-scale number-sense, we think Copilot in Excel with Python will improve analysis-sense for the world. […]
A Russian programmer accused of donating money to Ukraine had his Android device secretly implanted with spyware by the Federal Security Service (FSB) after he was detained earlier this year. The findings come as part of a collaborative investigation by First Department and the University of Toronto’s Citizen Lab. “The spyware placed on his device […]
Google Photos’ new 2024 Recap feature highlights memorable photos and insights about your year.
It’s been one year since Google launched Gemini 1.0 — and since then, developers have built everything from productivity apps to party games and accessibility tools. And…
Now celebrating 15 years of advancing cloud security, the Cloud Security Alliance (CSA) is proud to be the world’s leading organization dedicated to defining best practices for a secure cloud computing environment. Since our incorporation in 2009 and the release of our inaugural Security Guidance, CSA has expanded our impact through a broad portfolio of […]