After over 20 years of service, Microsoft is officially shutting down Skype in May, urging users to switch to Teams for calls and chats. The post Skype is dead after over 20 years, deprecated by Microsoft in May to make room for Teams appeared first on MSPoweruser.
Category Archives: News
OpenAI has finally made Sora, its AI video generator, available for folks in the EU and the UK two months after its initial launch. The post Sora is finally coming to EU and UK, two months after its launch appeared first on MSPoweruser.
Meta plans a standalone AI app in 2025, while Sam Altman humorously teases OpenAI’s potential competition in “social app.” The post Sam Altman jokingly teases OpenAI’s “social app” as Meta AI plans standalone app launch appeared first on MSPoweruser.
Mozilla’s updated Firefox terms grant them extensive rights over your data, including a broad license to use information for features. The post Folks are moving away from Firefox as Mozilla updates new ToS that could violate your privacy appeared first on MSPoweruser.
The hotly anticipated GPT-4.5 model has finally arrived as a research preview and will soon power OpenAI’s ChatGPT for everyone. The post OpenAI promises GPT-4.5 will “hallucinate less” appeared first on MSPoweruser.
Google has released patches for 43 vulnerabilities in Android’s March 2025 security update, including two zero-days. Serbian authorities have used one of the zero-days to unlock confiscated devices. […]
Credential stuffing attacks had a huge impact in 2024, fueled by a vicious circle of infostealer infections and data breaches. But things could be about to get worse still with Computer-Using Agents, a new kind of AI agent that enables low-cost, low-effort automation of common web tasks — including those frequently performed by attackers. Stolen […]
Threat hunters are calling attention to a new highly-targeted phishing campaign that singled out “fewer than five” entities in the United Arab Emirates (U.A.E.) to deliver a previously undocumented Golang backdoor dubbed Sosano. The malicious activity was specifically directed against aviation and satellite communications organizations, according to Proofpoint, which detected it in late October
Internet service providers (ISPs) in China and the West Coast of the United States have become the target of a mass exploitation campaign that deploys information stealers and cryptocurrency miners on compromised hosts. The findings come from the Splunk Threat Research Team, which said the activity also led to the delivery of various binaries that […]
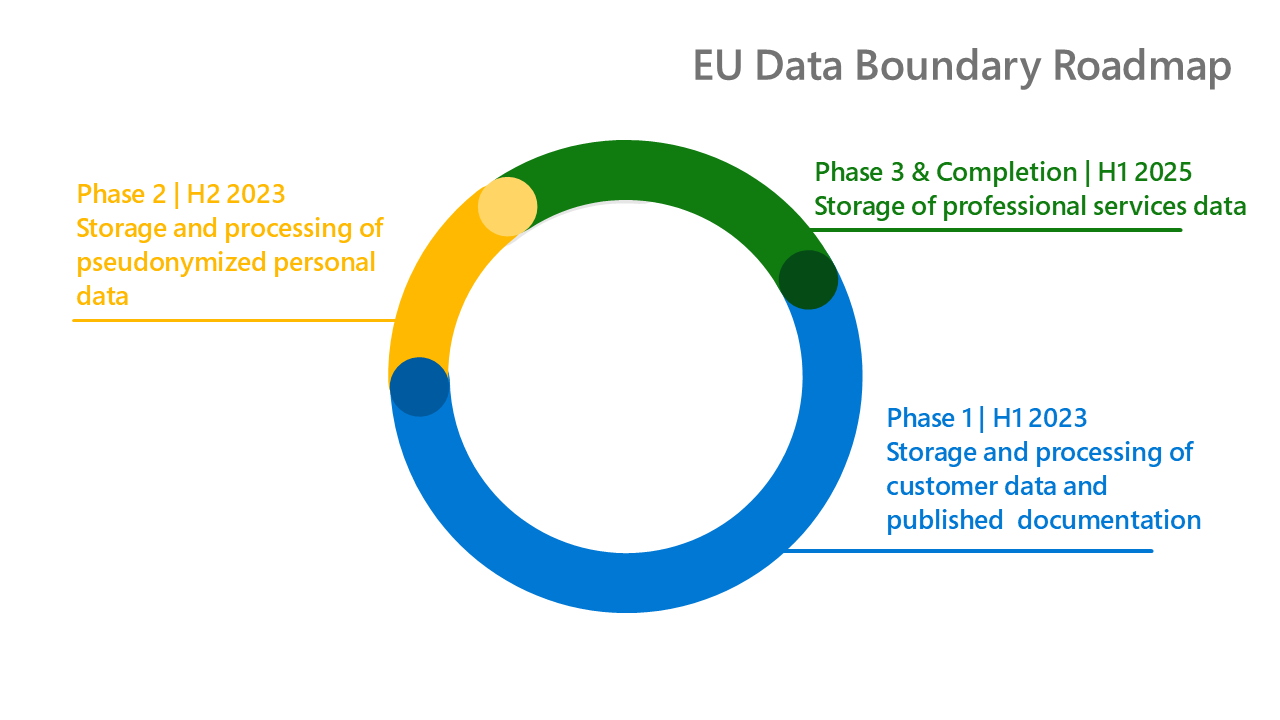
At Microsoft, we remain committed to enabling European businesses to thrive by providing the tools and support necessary to drive their success and give our customers throughout the European Union more control over their data. To fulfill these goals, today Microsoft is announcing that it has completed the EU Data Boundary for the Microsoft Cloud, an […]