The ubiquitous ESP32 microchip made by Chinese manufacturer Espressif and used by over 1 billion units as of 2023 contains an undocumented backdoor that could be leveraged for attacks. […]
Category Archives: News
Cybercriminals are sending bogus copyright claims to YouTubers to coerce them into promoting malware and cryptocurrency miners on their videos. […]
See how we’re celebrating International Women’s Day and Women’s History Month across our products
In September 2023, KrebsOnSecurity published findings from security researchers who concluded that a series of six-figure cyberheists across dozens of victims resulted from thieves cracking master passwords stolen from the password manager service LastPass in 2022. In a court filing this week, U.S. federal agents investigating a spectacular $150 million cryptocurrency heist said they had […]
U.S. authorities have seized over $23 million in cryptocurrency linked to the theft of $150 million from a Ripple crypto wallet in January 2024. Investigators believe hackers who breached LastPass in 2022 were behind the attack. […]
A critical command injection vulnerability impacting the Edimax IC-7100 IP camera is currently being exploited by botnet malware to compromise devices. […]
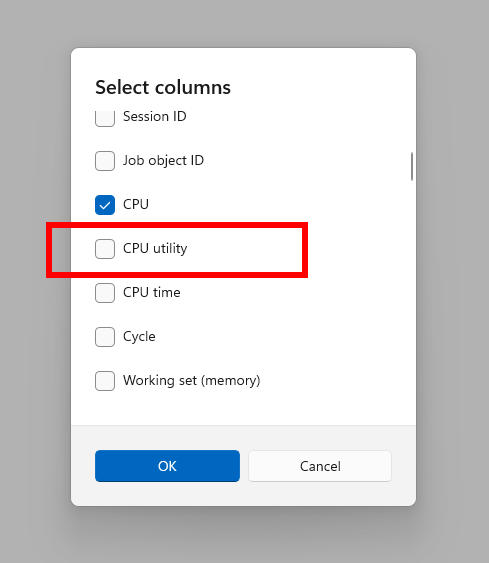
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 27808 to the Canary Channel. We are also not planning to release SDKs for 27xxx series builds for the time being. Changes and Improvements [Task Manager] We are beginning to roll out a change to the way Task Manager calculates CPU utilization for […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 22635.5025 (KB5053661) to the Beta Channel. Please note this build will only be provided to Windows Insiders in the Beta Channel who did not upgrade to receiving updates based on Windows 11, version 24H2. Changes in Beta Channel builds and updates are documented in […]
A Memphis man was arrested and charged with stealing DVDs and Blu-ray discs of unreleased movies and sharing ripped digital copies online before their release. […]
The administrators of the Russian Garantex crypto-exchange have been charged in the United States with facilitating money laundering for criminal organizations and violating sanctions. […]