Legislation would share kids’ information without parental consent or rules on how it’s used; we have a better way to keep kids safe.
Category Archives: News
A new Android spyware named ‘KoSpy’ is linked to North Korean threat actors who have infiltrated Google Play and third-party app store APKPure through at least five malicious apps. […]
Indian authorities arrested Aleksej Besciokov, the co-founder and one of the administrators of the Russian Garantex crypto-exchange while vacationing with his family in Varkala, India. […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 27813 to the Canary Channel. We are also not planning to release SDKs for 27xxx series builds for the time being. Changes and Improvements [General] This update includes a small set of general improvements and fixes that improve the overall experience for Insiders […]
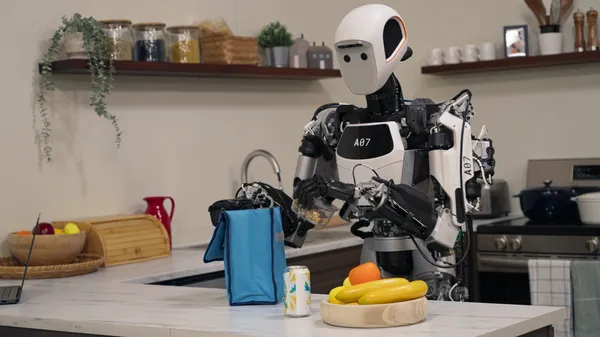
Today, Google DeepMind announced a new family of Gemini models designed for robotics. Gemini Robotics is a vision-language-action (VLA) model that takes natural language…
Google DeepMind is announcing two new models, based on Gemini 2.0, that are designed for robotics.Gemini Robotics is our most advanced vision-language-action model, whic…
Mozilla is warning Firefox users to update their browsers to the latest version to avoid facing disruption and security risks caused by the upcoming expiration of one of the company’s root certificates. […]
Slovak cybersecurity company ESET says a newly patched zero-day vulnerability in the Windows Win32 Kernel Subsystem has been exploited in attacks since March 2023. […]
The China-nexus cyber espionage group tracked as UNC3886 has been observed targeting end-of-life MX routers from Juniper Networks as part of a campaign designed to deploy custom backdoors, highlighting their ability to focus on internal networking infrastructure. “The backdoors had varying custom capabilities, including active and passive backdoor functions, as well as an embedded script […]
Traditional Data Loss Prevention (DLP) solutions weren’t built for today’s browser-driven workplace. Now sensitive data moves moves through SaaS apps, AI tools, and personal accounts, bypassing legacy security controls. Learn from Keep Aware how real-time browser security can stop data leaks before they happen. […]