Google’s President of Global Affairs, Kent Walker, gives an overview of Google’s approach to creative content and AI training.
Category Archives: News
Google has set out a balanced approach for the responsible use of content in AI, designed to further cooperation and help build a thriving AI ecosystem.In the UK, the De…
The openSNP project, a platform for sharing genetic and phenotypic data, will shut down on April 30, 2025, and delete all user submissions over privacy concerns and the risk of misuse by authoritarian governments. […]
A vulnerability in Verizon’s Call Filter feature allowed customers to access the incoming call logs for another Verizon Wireless number through an unsecured API request. […]
NotebookLM has launched Discover Sources, which lets you add sources from the web to your notebook.
Over 39 million secrets like API keys and account credentials were leaked on GitHub throughout 2024, exposing organizations and users to significant security risks. […]
Microsoft has announced that hotpatch updates are now available for business customers using Windows 11 Enterprise 24H2 on x64 (AMD/Intel) systems, starting today. […]
Royal Mail is investigating claims of a security breach after a threat actor leaked over 144GB of data allegedly stolen from the company’s systems. […]
The 2025 Coachella music festival will once again be livestreamed exclusively on YouTube, starting Friday, April 11th at 4 PM PT/7 PM ET. The livestream will include six…
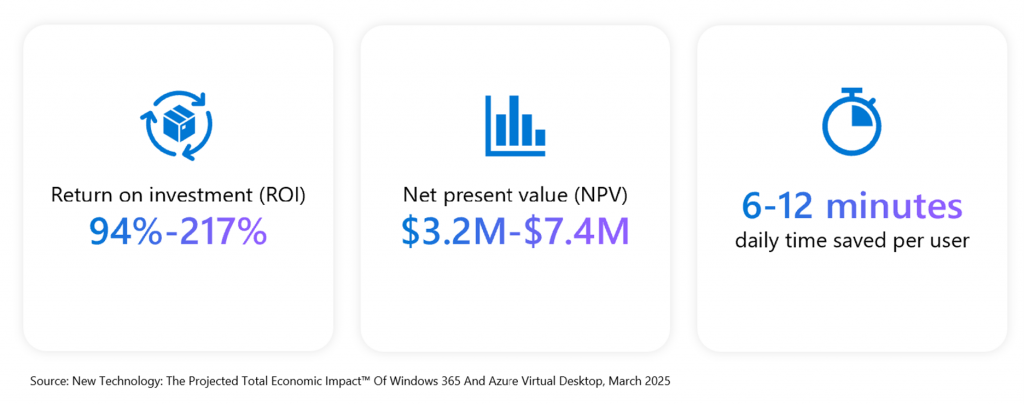
In today’s dynamic work environment, businesses need robust solutions that support resilience and maximize return on investment (ROI). As organizations modernize their IT environments, they increasingly turn to cloud solutions like Windows 365 to enhance security and productivity, streamline IT management and ensure seamless connectivity. We are thrilled to announce the general availability of our […]