The Russian government has introduced a new law that makes installing a tracking app mandatory for all foreign nationals in the Moscow region. […]
Category Archives: Mobile
Auto Added by WPeMatico
Wisconsin wireless provider Cellcom has confirmed that a cyberattack is responsible for the widespread service outage and disruptions that began on the evening of May 14, 2025. […]
The Windows developer platform continues to evolve, bringing more quality, performance and innovation through Copilot+ PC. This translates into a tremendous opportunity for app developers that are looking to scale their user acquisition strategies, to deepen engagement, to invent on larger form factors where immersive experiences thrive. It’s been exciting to witness the momentum and […]
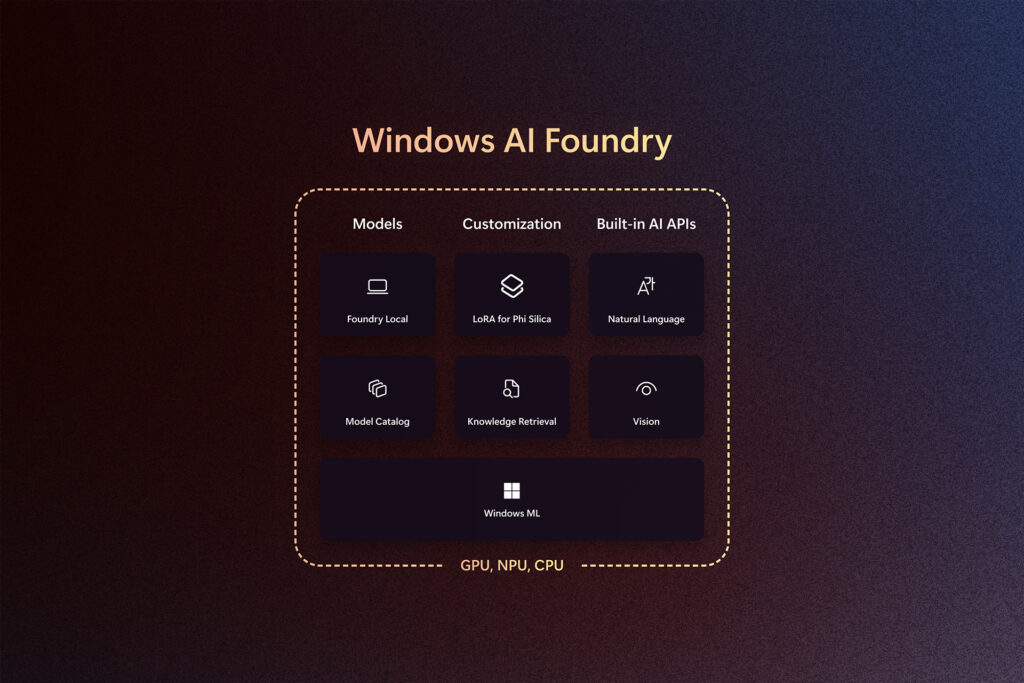
We’re excited to be back at Build, a special moment each year to connect with the global developer community. It’s energizing to share what we’ve been working on, and just as important, to hear how developers are using Microsoft platforms to build what’s next. At Microsoft, we believe the future of AI is being built […]
Today, we’re excited to announce three major enhancements to model fine-tuning in Azure AI Foundry—Reinforcement Fine-Tuning (RFT) with o4-mini (coming soon), Supervised Fine-Tuning (SFT) for the GPT-4.1-nano and Llama 4 Scout model (available now). These updates reflect our continued commitment to empowering organizations with tools to build highly customized, domain-adapted AI systems for real-world impact. […]
Google is announcing improvements for the Advanced Protection feature in Android 16 that strengthen defenses against sophisticated spyware attacks. […]
Google has released the May 2025 security updates for Android with fixes for 45 security flaws, including an actively exploited zero-click FreeType 2 code execution vulnerability. […]
Microsoft has announced that it will discontinue the password storage and autofill feature in the Authenticator app starting in July and will complete the deprecation in August 2025. […]
In these uncertain times, marked by fluctuating economic conditions and supply chain concerns, businesses face numerous challenges. Amidst these complexities, it is even more important to adopt new technologies in the age of AI to stay competitive and secure. According to the 2025 Work Trend Index report, 82% of leaders say this is a pivotal year […]
A new Android malware has been discovered hidden inside trojanized versions of the Alpine Quest mapping app, which is reportedly used by Russian soldiers as part of war zone operational planning. […]