A new phishing campaign targets Counter-Strike 2 players utilizing Browser-in-the-Browser (BitB) attacks that display a realistic window that mimics Steam’s login page. […]
Author Archives: [email protected]
Written by Kurt Seifried, Chief Innovation Officer, CSA. The Story That Shook the Markets In January 2025, a relatively unknown Chinese AI company called DeepSeek burst onto the global stage with a bold claim—they had built advanced AI models that matched or exceeded the capabilities of tech giants like OpenAI and Google—at a tiny fraction of […]
New Android malware campaigns use Microsoft’s cross-platform framework .NET MAUI while disguising as legitimate services to evade detection. […]
A new investigation has unearthed nearly 200 unique command-and-control (C2) domains associated with a malware called Raspberry Robin. “Raspberry Robin (also known as Roshtyak or Storm-0856) is a complex and evolving threat actor that provides initial access broker (IAB) services to numerous criminal groups, many of which have connections to Russia,” Silent Push said in […]
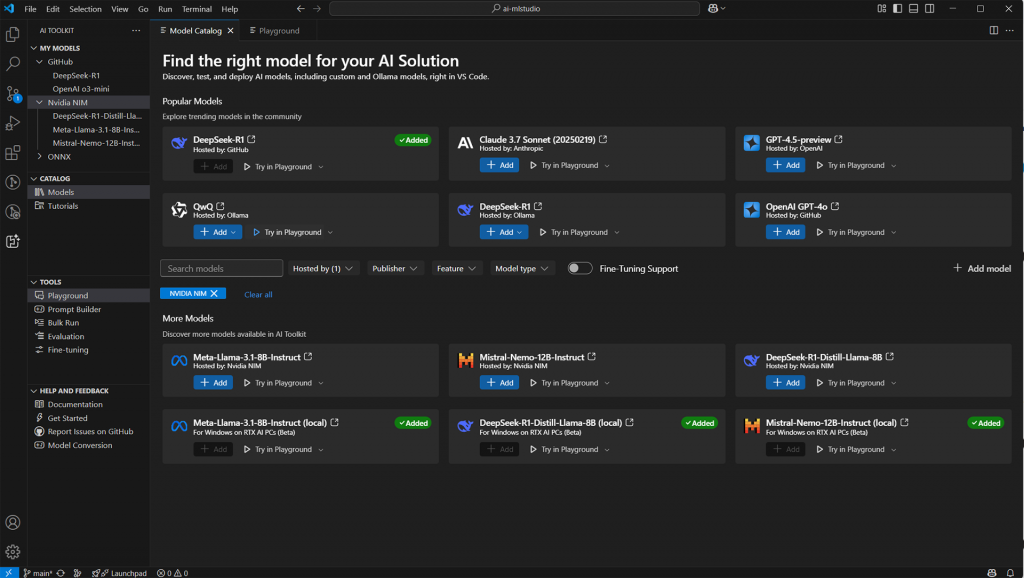
AI Toolkit now supports NVIDIA NIM microservice-based foundation models for inference testing in the model playground! Explore these NIMs in AI Toolkit’s model catalog today! Read more about it on the Tech Community Blog at aka.ms/aitk/nimsblog.
A major telecommunications company located in Asia was allegedly breached by Chinese state-sponsored hackers who spent over four years inside its systems, according to a new report from incident response firm Sygnia. The cybersecurity company is tracking the activity under the name Weaver Ant, describing the threat actor as stealthy and highly persistent. The name […]
Organizations now use an average of 112 SaaS applications—a number that keeps growing. In a 2024 study, 49% of 644 respondents who frequently used Microsoft 365 believed that they had less than 10 apps connected to the platform, despite the fact that aggregated data indicated over 1,000+ Microsoft 365 SaaS-to-SaaS connections on average per deployment. […]
Cybersecurity researchers are calling attention to an Android malware campaign that leverages Microsoft’s .NET Multi-platform App UI (.NET MAUI) framework to create bogus banking and social media apps targeting Indian and Chinese-speaking users. “These threats disguise themselves as legitimate apps, targeting users to steal sensitive information,” McAfee Labs researcher Dexter Shin said. .NET
Law enforcement authorities in seven African countries have arrested 306 suspects and confiscated 1,842 devices as part of an international operation codenamed Red Card that took place between November 2024 and February 2025. The coordinated effort “aims to disrupt and dismantle cross-border criminal networks which cause significant harm to individuals and businesses,” INTERPOL said, adding […]
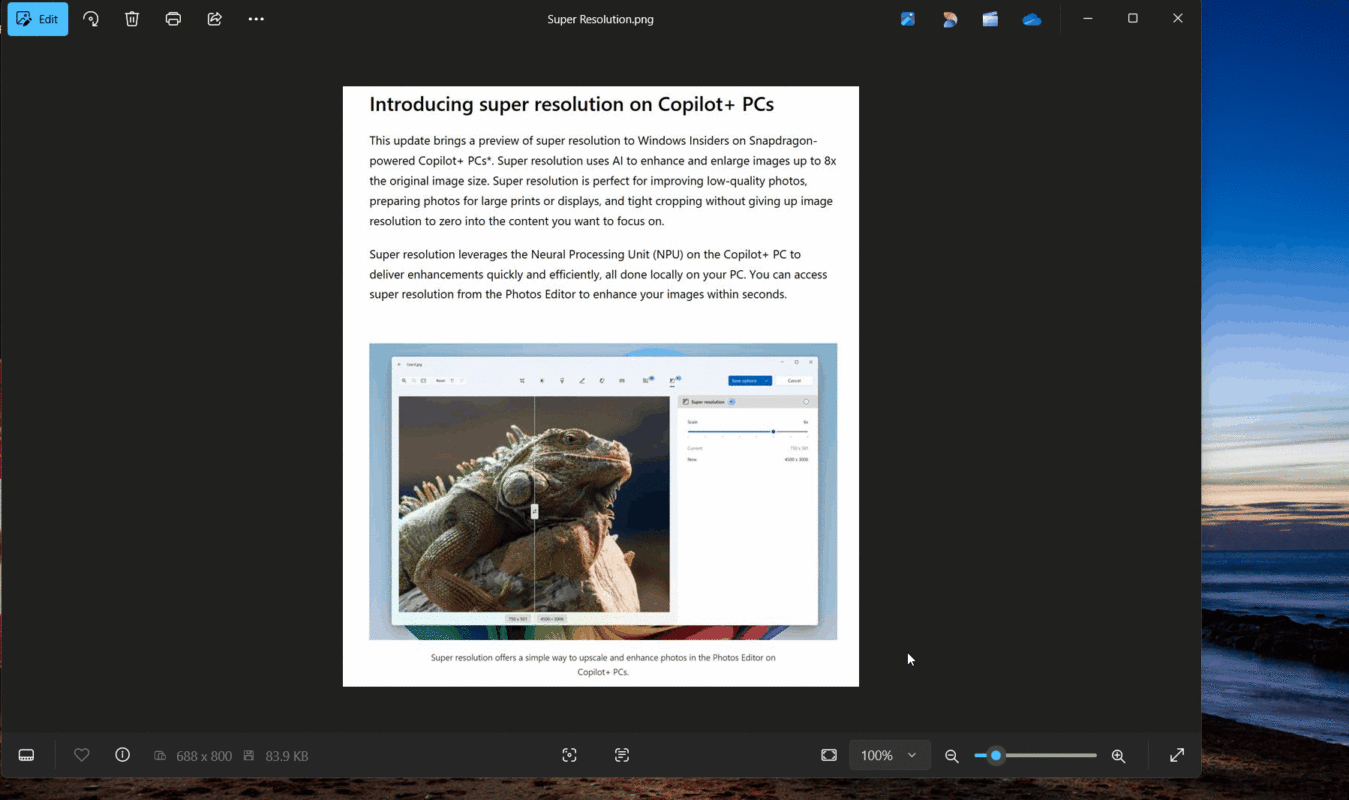
Hello Windows Insiders, Today we are beginning to roll out a Microsoft Photos app update to Windows Insiders on Windows 11 across all Insider Channels and also to Windows Insiders on Windows 10 in the Release Preview Channel. Not all Insiders will see this update right away or the features noted below as we roll […]