Broadcom released security updates today to fix a high-severity authentication bypass vulnerability in VMware Tools for Windows. […]
Author Archives: [email protected]
Free unofficial patches are available for a new Windows zero-day vulnerability that can let remote attackers steal NTLM credentials by tricking targets into viewing malicious files in Windows Explorer. […]
On the Android Developers Blog, we’re sharing how we’re making it easier than ever for developers to build safe apps, while also continuing to strengthen our ecosys…
Gemini 2.5 is our most intelligent AI model, now with thinking.
A threat actor known as EncryptHub has been linked to Windows zero-day attacks exploiting a Microsoft Management Console vulnerability patched this month. […]
A new phishing campaign targets Counter-Strike 2 players utilizing Browser-in-the-Browser (BitB) attacks that display a realistic window that mimics Steam’s login page. […]
Written by Kurt Seifried, Chief Innovation Officer, CSA. The Story That Shook the Markets In January 2025, a relatively unknown Chinese AI company called DeepSeek burst onto the global stage with a bold claim—they had built advanced AI models that matched or exceeded the capabilities of tech giants like OpenAI and Google—at a tiny fraction of […]
New Android malware campaigns use Microsoft’s cross-platform framework .NET MAUI while disguising as legitimate services to evade detection. […]
A new investigation has unearthed nearly 200 unique command-and-control (C2) domains associated with a malware called Raspberry Robin. “Raspberry Robin (also known as Roshtyak or Storm-0856) is a complex and evolving threat actor that provides initial access broker (IAB) services to numerous criminal groups, many of which have connections to Russia,” Silent Push said in […]
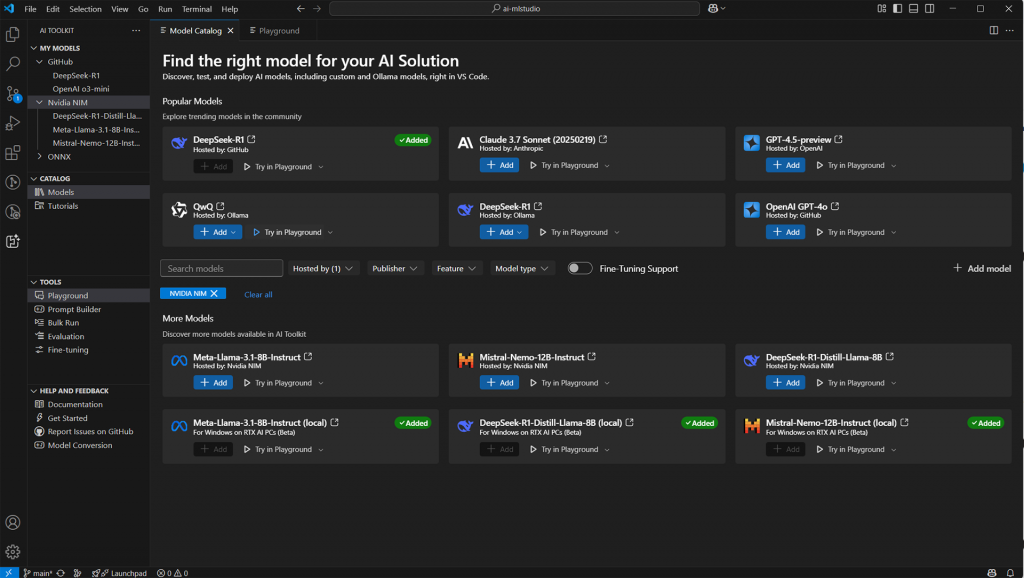
AI Toolkit now supports NVIDIA NIM microservice-based foundation models for inference testing in the model playground! Explore these NIMs in AI Toolkit’s model catalog today! Read more about it on the Tech Community Blog at aka.ms/aitk/nimsblog.