Are you looking for a comprehensive Icecream Ebook Reader review? This program prides itself on being a feature-rich solution for ebook management and reading. However, does it genuinely fulfill its promises? In this article, I’ll discuss the features and what you should know about the program. Let’s delve straight into it! Pros Cons You can […]
Author Archives: [email protected]
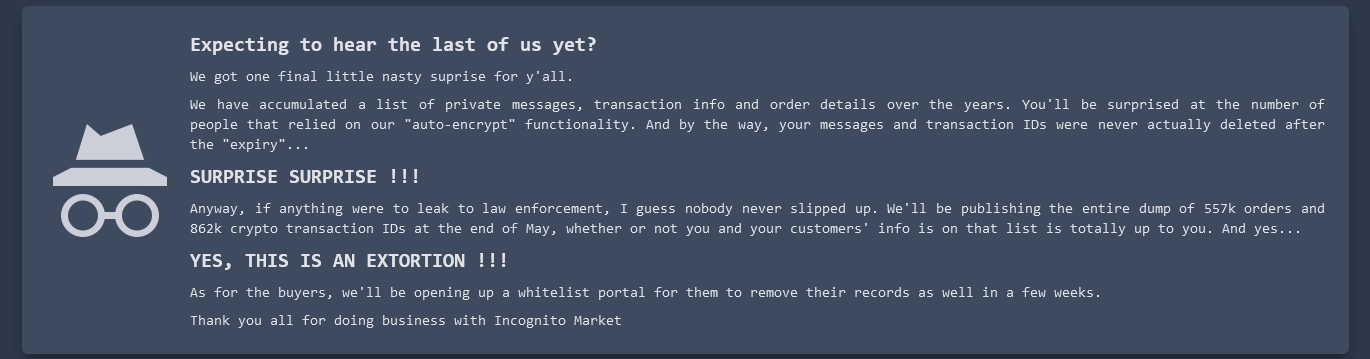
Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors and buyers, threatening to publish cryptocurrency transaction and chat records of users who refuse to pay a fee ranging from $100 to $20,000. The bold mass extortion attempt comes just days after Incognito Market administrators […]
In collaboration with cross-industry browser vendors under the Speedometer governance policy, the Microsoft Edge team is very excited to have contributed to the recently released version 3.0 of Speedometer, as announced on browserbench.org. First released in 2014, Speedometer is a popular browser benchmark and a key driver of recent browser performance improvements. Version 3.0 has […]
Looking for an Article Forge review so you can start your AI-powered writing journey? You’re in the right place, as I’ve already used, tested, and generated with Article Forge and have so much to share. Let’s jump right into it and discover what comes with this tool and if it’s worth it! What Is Article […]
If you’re looking for a professional interior design app, this Remodel AI review will help you decide if that’s the one. It aims to give you an entry into home design even if you’re a complete rookie. But does it achieve it? I tested the tool inside and out to give you an answer. I’ll […]
Originally published by Adaptive Shield.Written by Hananel Livneh.In recent weeks, a concerning wave of cyber attacks has been targeting Microsoft Azure environments, compromising crucial user accounts, including those of senior executives. Proofpoint researchers have identified an ongoing malicious campaign, which utilizes sophisticated techniques like credential phishing and cloud account takeover (ATO). This blog post will […]
ORLANDO, Fla. — March 11, 2024 — Monday, at the HIMSS 2024 Global Health Conference, a new consortium of healthcare leaders announced the creation of the Trustworthy & Responsible AI Network (TRAIN), which aims to operationalize responsible AI principles to improve the quality, safety and trustworthiness of AI in health. Members of the network include […]
The developers of the Leather cryptocurrency wallet are warning of a fake app on the Apple App Store, with users reporting it is a wallet drainer that stole their digital assets. […]
As cyber threats loom around every corner and privileged accounts become prime targets, the significance of implementing a robust Privileged Access Management (PAM) solution can’t be overstated. With organizations increasingly migrating to cloud environments, the PAM Solution Market is experiencing a transformative shift toward cloud-based offerings. One Identity PAM Essentials stands
Users in Brazil are the target of a new banking trojan known as CHAVECLOAK that’s propagated via phishing emails bearing PDF attachments. “This intricate attack involves the PDF downloading a ZIP file and subsequently utilizing DLL side-loading techniques to execute the final malware,” Fortinet FortiGuard Labs researcher Cara Lin said. The attack chain involves the use of