Originally published by Schellman. Written by Austin Bentley. It’s no secret: many organizations view and treat phishing as a periodic checkbox assessment. It’s often a basic email template sent to an entire organization. If someone clicks the link, they are recorded and possibly enrolled in training. While this approach can certainly check the “quarterly […]
Author Archives: [email protected]
Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a Linux asynchronous I/O mechanism called io_uring to bypass traditional system call monitoring. This causes a “major blind spot in Linux runtime security tools,” ARMO said. “This mechanism allows a user application to perform various actions without using system calls,” the company said […]
As many as 159 CVE identifiers have been flagged as exploited in the wild in the first quarter of 2025, up from 151 in Q4 2024. “We continue to see vulnerabilities being exploited at a fast pace with 28.3% of vulnerabilities being exploited within 1-day of their CVE disclosure,” VulnCheck said in a report shared […]
A significant security gap in Linux runtime security caused by the ‘io_uring’ interface allows rootkits to operate undetected on systems while bypassing advanced Enterprise security software. […]
The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to their cybercrime suite with generative artificial intelligence (GenAI) capabilities. “This addition lowers the technical barrier for creating phishing pages, enabling less tech-savvy criminals to deploy customized scams in minutes,” Netcraft said in a new report shared with The Hacker News. “
The Evolving Healthcare Cybersecurity Landscape Healthcare organizations face unprecedented cybersecurity challenges in 2025. With operational technology (OT) environments increasingly targeted and the convergence of IT and medical systems creating an expanded attack surface, traditional security approaches are proving inadequate. According to recent statistics, the healthcare sector
A critical security flaw has been disclosed in the Commvault Command Center that could allow arbitrary code execution on affected installations. The vulnerability, tracked as CVE-2025-34028, carries a CVSS score of 9.0 out of a maximum of 10.0. “A critical security vulnerability has been identified in the Command Center installation, allowing remote attackers to execute […]
Using AI to generate ‘synthetic memories’ to explore new ways of supporting dementia care. An art & research collaboration into reminiscence therapy visuals.
WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy that allows users to block participants from sharing the contents of a conversation in traditional chats and groups. “This new setting available in both chats and groups helps prevent others from taking content outside of WhatsApp for when you may want extra privacy,” […]
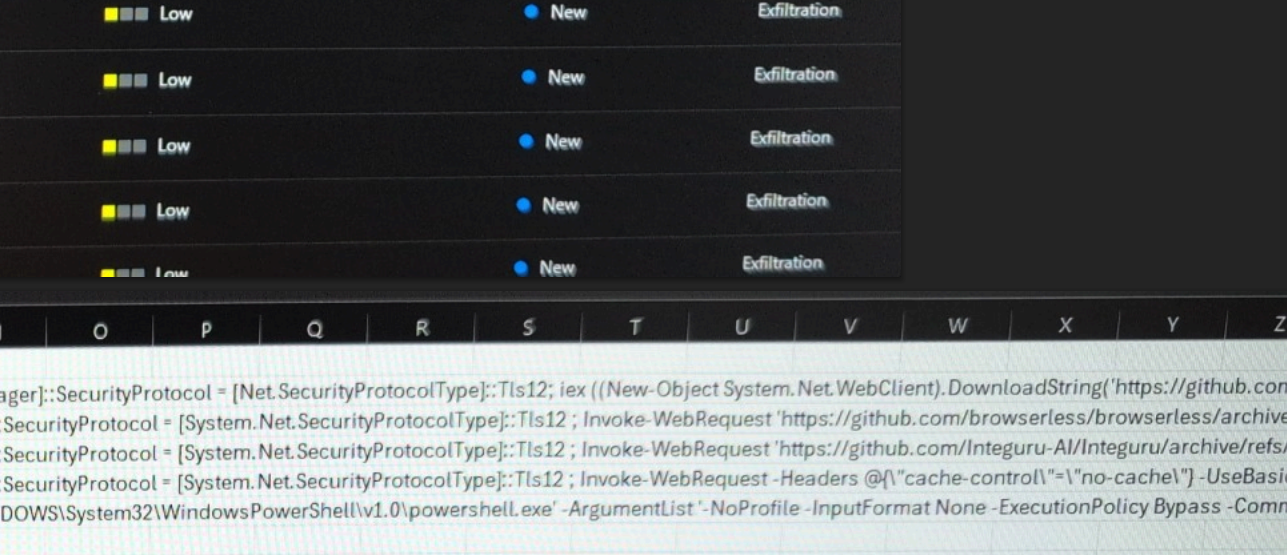
A Little Sunshine, async-ip-rotator, Browserless, Daniel J. Berulis, Department of Government Efficiency, Department of Health and Human Services, DOGE, Ge0rg3, Github, Integuru, Krebs, Labor Department, Marko Elez, National Labor Relations Board, News, Politico, Security, The Coming Storm, The Wall Street Journal
DOGE Worker’s Code Supports NLRB Whistleblower
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency’s sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one […]