In an era where digital innovation is king, the integration of Microsoft Azure OpenAI Service is cutting through the static of the telecommunications sector. Industry leaders like Windstream, AudioCodes, AT&T, and Vodafone are leveraging AI to better engage with their customers and streamline their operations. These companies are pioneering the use of AI to not […]
Author Archives: [email protected]
Transforming care for patients and providers alike with Azure OpenAI Service In the rapidly evolving landscape of healthcare, the integration of artificial intelligence (AI) isn’t a futuristic vision: It’s a present reality. Azure OpenAI Service is supporting the way care is delivered and experienced by patients and providers alike. As healthcare providers and tech companies […]
Japanese police placed fake payment cards in convenience stores to protect the elderly targeted by tech support scams or unpaid money fraud. […]
Okta warns of an “unprecedented” spike in credential stuffing attacks targeting its identity and access management solutions, with some customer accounts breached in the attacks. […]
Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“signal-2023-12-20-160512.ppsx”) as the starting point, with
An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these fraudulent interviews, the developers are often asked
Innovate. Connect. Cultivate. The Cloud Cultures series is an exploration of the intersection between cloud innovation and culture across the globe. ‘Mottainai,’ an idea deeply rooted in Japanese culture, is a call to respect resources and avoid waste. It goes beyond mere frugality; it’s an inherent recognition of the value of each item. I saw […]
Welcome to Cyber Security Today. This is the Week in Review for the week ending Friday April 26, 2024. From Toronto, I’m Howard Solomon. In a few minutes David Shipley, head of Beauceron Security, will be here to discuss some of the biggest news of the past week. They include the latest developments in the […]
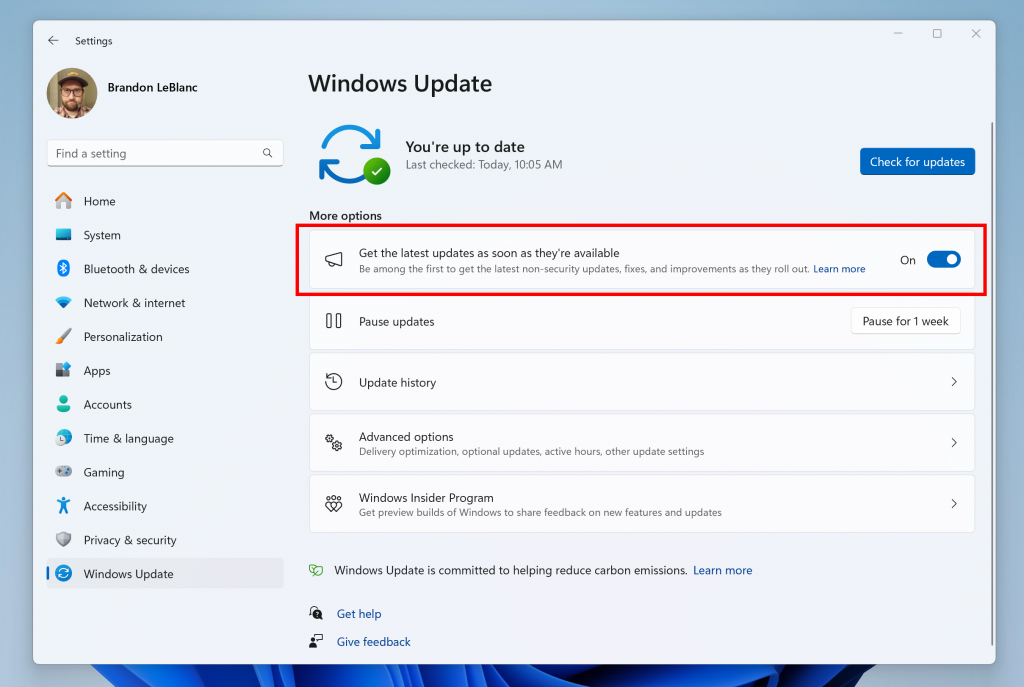
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 22635.3566 (KB5037002) to the Beta Channel. REMINDER: All Windows Insiders in the Beta Channel will now be on the same build (Build 22635.xxxx) via an enablement package. For Windows Insiders in the Beta Channel who want to be the first to get features gradually […]
Over the past 18 months, AI has augmented and inspired the work of many creative professionals. At the same time, many are concerned about the effects of this technology…