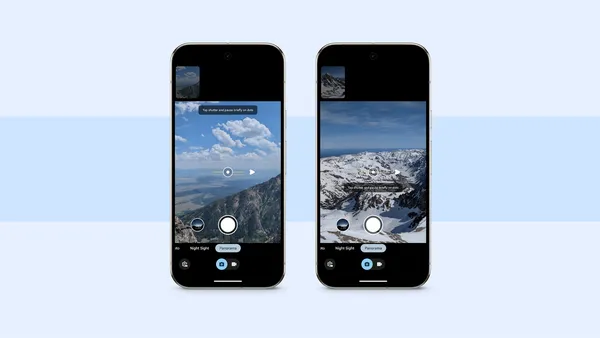
Learn more about Google Pixel’s new panorama mode as well as three tips on using it.
Author Archives: [email protected]
Seven malicious PyPi packages were found using Gmail’s SMTP servers and WebSockets for data exfiltration and remote command execution. […]
Anyone in the U.S. can now get immediate access to AI Mode in Labs.
Cybersecurity researchers have shed light on a new campaign targeting WordPress sites that disguises the malware as a security plugin. The plugin, which goes by the name “WP-antymalwary-bot.php,” comes with a variety of features to maintain access, hide itself from the admin dashboard, and execute remote code. “Pinging functionality that can report back to a […]
In these uncertain times, marked by fluctuating economic conditions and supply chain concerns, businesses face numerous challenges. Amidst these complexities, it is even more important to adopt new technologies in the age of AI to stay competitive and secure. According to the 2025 Work Trend Index report, 82% of leaders say this is a pivotal year […]
This Asian American, Native Hawaiian, and Pacific Islander Heritage Month, Google’s products can help you embrace the spirit of connection and celebration
Security Operations Center (SOC) teams are facing a fundamentally new challenge — traditional cybersecurity tools are failing to detect advanced adversaries who have become experts at evading endpoint-based defenses and signature-based detection systems. The reality of these “invisible intruders” is driving a significant need for a multi-layered approach to detecting threats,
Artificial intelligence (AI) company Anthropic has revealed that unknown threat actors leveraged its Claude chatbot for an “influence-as-a-service” operation to engage with authentic accounts across Facebook and X. The sophisticated activity, branded as financially-motivated, is said to have used its AI tool to orchestrate 100 distinct persons on the two social media platforms, creating a
Originally Published by Abnormal AI. Written by Richard Orange. We hired an ethical hacker to stage real-time social engineering attacks with AI powering the engine. The results confirm that it’s a golden age for scammers… and show you exactly where to put your cyber security budget in 2025. Anyone who has worked at a major […]
For over a decade, application security teams have faced a brutal irony: the more advanced the detection tools became, the less useful their results proved to be. As alerts from static analysis tools, scanners, and CVE databases surged, the promise of better security grew more distant. In its place, a new reality took hold—one defined […]