Google is announcing a new paper and support for an effort to train 100,000 electrical workers and 30,000 new apprentices in the United States.
Author Archives: [email protected]
WhatsApp has announced the introduction of ‘Private Processing,’ a new technology that enables users to utilize advanced AI features by offloading tasks to privacy-preserving cloud servers. […]
Cybersecurity company SonicWall has warned customers that several vulnerabilities impacting its Secure Mobile Access (SMA) appliances are now being actively exploited in attacks. […]
Commvault, a leading provider of data protection solutions, says a nation-state threat actor who breached its Azure environment didn’t gain access to customer backup data. […]
The FBI has shared 42,000 phishing domains tied to the LabHost cybercrime platform, one of the largest global phishing-as-a-service (PhaaS) platforms that was dismantled in April 2024. […]
As the field of artificial intelligence (AI) continues to evolve at a rapid pace, new research has found how techniques that render the Model Context Protocol (MCP) susceptible to prompt injection attacks could be used to develop security tooling or identify malicious tools, according to a new report from Tenable. MCP, launched by Anthropic in […]
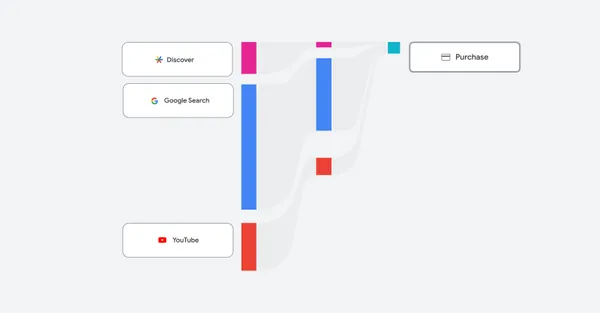
An overview of the latest reporting features, including channel performance reporting, coming to Performance Max.
British supermarket chain Co-op Food has confirmed to BleepingComputer via a statement that it has suffered limited operational disruption as it responds to a cyberattack. […]
Ascension, one of the largest private healthcare systems in the United States, is notifying patients that their personal and health information was stolen in a December 2024 data theft attack, which affected a former business partner. […]
Originally published by CXO REvolutionaries. Written by Jay Patty, CTO in Residence, Zscaler. Know the difference between vendor-related and technology-related problems to determine the fastest resolution. Thomas Jefferson famously proclaimed that all men are created equal, but he would agree that today’s technical problems are not. Some are tied to the quirks of a […]