Epic’s proposed changes to Android and Google Play would harm consumers, developers and device manufacturers.
Author Archives: [email protected]
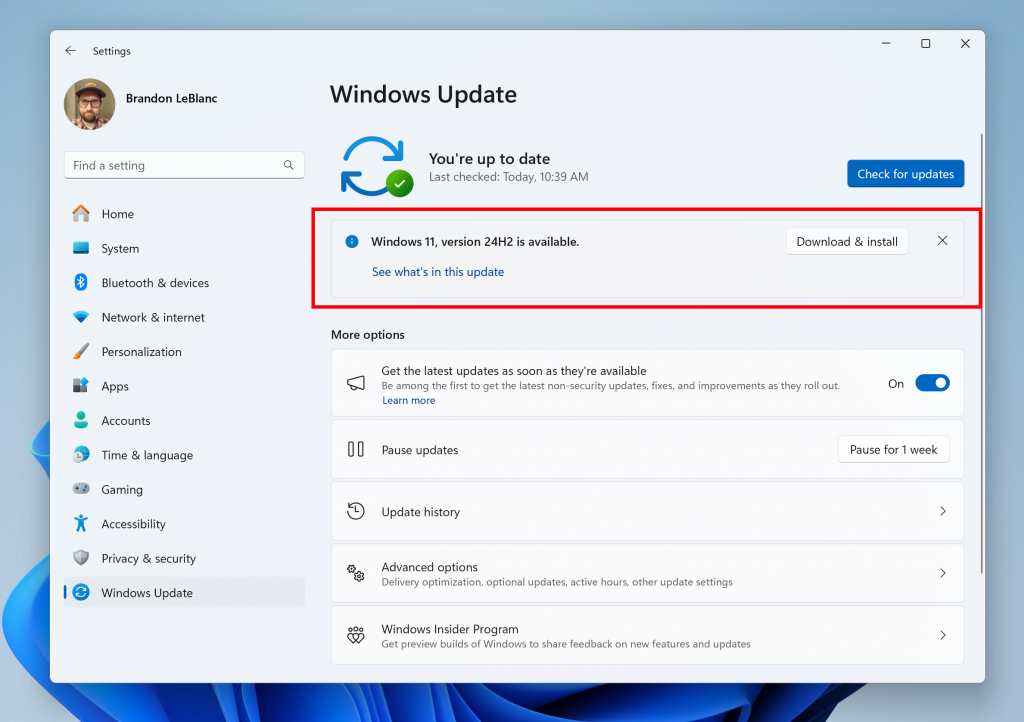
Microsoft is rolling out Windows 11 24H2 to testers in the Release Preview Channel, confirming that it is in the final stages of testing. […]
Microsoft announced today that it will start deprecating VBScript in the second half of 2024 by making it an on-demand feature until it’s completely removed. […]
Hello Windows Insiders! Today, we are making this year’s annual feature update Windows 11, version 24H2 (Build 26100.712) available in the Release Preview Channel for customers to preview ahead of general availability later this calendar year. Windows 11, version 24H2* includes a range of new features such as the HDR background support, energy saver, Sudo […]
Security researchers are warning that China-linked state-backed hackers are increasingly relying on vast proxy networks of virtual private servers and compromised connected devices for cyberespionage operations. […]
At a press event early this week, Microsoft announced a new category of PCs called Copilot+ PCs. These new PCs will be thin, light, and beautiful and they are the most powerful Windows PCs ever built. These new Copilot+ PCs will have at least 16GB of RAM, NPU with 40+ TOPS performance and at least […]
Amazon is giving Alexa a major upgrade later in 2024, with plans to make the voice assistant more conversational by incorporating generative AI features. The new Alexa is expected to be more than just a smart speaker for setting alarms and playing music. Generative AI will help in for more natural and engaging two-way conversations, […]
The Intercontinental Exchange (ICE) will pay a $10 million penalty to settle charges brought by the U.S. Securities and Exchange Commission (SEC) after failing to ensure its subsidiaries promptly reported an April 2021 VPN security breach. […]
LastPass announced it will start encrypting URLs stored in user vaults for enhanced privacy and protection against data breaches and unauthorized access. […]
Redmond giant Microsoft might be prepping a massive $16 billion offer to acquire Valve, according to a rumor on X. The news comes from a content creator focused on Counter-Strike, but neither Valve nor Microsoft have commented on the speculation. Valve, known for its PC gaming platform Steam and titles like Dota 2 and Counter-Strike. Valuation […]