Russia-aligned hacktivists persistently target key public and private organizations in the Netherlands with distributed denial of service (DDoS) attacks, causing access problems and service disruptions. […]
Author Archives: [email protected]
A Ukrainian national has been extradited from Spain to the United States to face charges over allegedly conducting Nefilim ransomware attacks against companies. […]
London’s iconic department store, Harrods, has confirmed it was targeted in a cyberattack, becoming the third major UK retailer to report cyberattacks in a week following incidents at M&S and the Co-op. […]
Here are 4 new ways it’s faster and easier than ever to set up your new Google TV device:No app download needed. Android phones will automatically show a notification up…
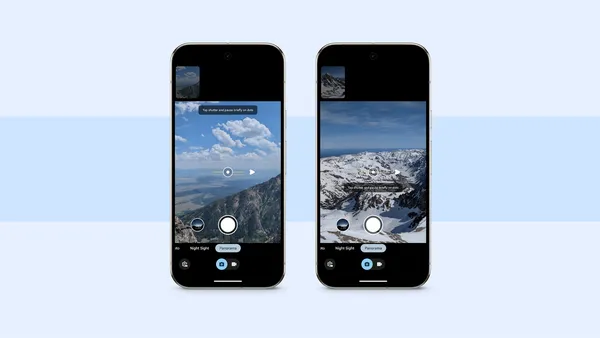
Learn more about Google Pixel’s new panorama mode as well as three tips on using it.
Seven malicious PyPi packages were found using Gmail’s SMTP servers and WebSockets for data exfiltration and remote command execution. […]
Anyone in the U.S. can now get immediate access to AI Mode in Labs.
Cybersecurity researchers have shed light on a new campaign targeting WordPress sites that disguises the malware as a security plugin. The plugin, which goes by the name “WP-antymalwary-bot.php,” comes with a variety of features to maintain access, hide itself from the admin dashboard, and execute remote code. “Pinging functionality that can report back to a […]
In these uncertain times, marked by fluctuating economic conditions and supply chain concerns, businesses face numerous challenges. Amidst these complexities, it is even more important to adopt new technologies in the age of AI to stay competitive and secure. According to the 2025 Work Trend Index report, 82% of leaders say this is a pivotal year […]
This Asian American, Native Hawaiian, and Pacific Islander Heritage Month, Google’s products can help you embrace the spirit of connection and celebration