Live Nation has confirmed that Ticketmaster suffered a data breach after its data was stolen from a third-party cloud database provider, which is believed to be Snowflake. […]
Author Archives: [email protected]
Japanese bitcoin exchange DMM Bitcoin is warning that 4,502.9 Bitcoin (BTC), or approximately $308 million (48.2 billion yen), has been stolen from one of its wallets today, making it the most significant cryptocurrency heist of 2024. […]
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added two vulnerabilities in its Known Exploited Vulnerabilities (KEV) catalog, including a Linux kernel privilege elevation flaw. […]
A threat actor claiming recent Santander and Ticketmaster breaches says they stole data after hacking into an employee’s account at cloud storage company Snowflake. However, Snowflake disputes these claims, saying recent breaches were caused by poorly secured customer accounts. […]
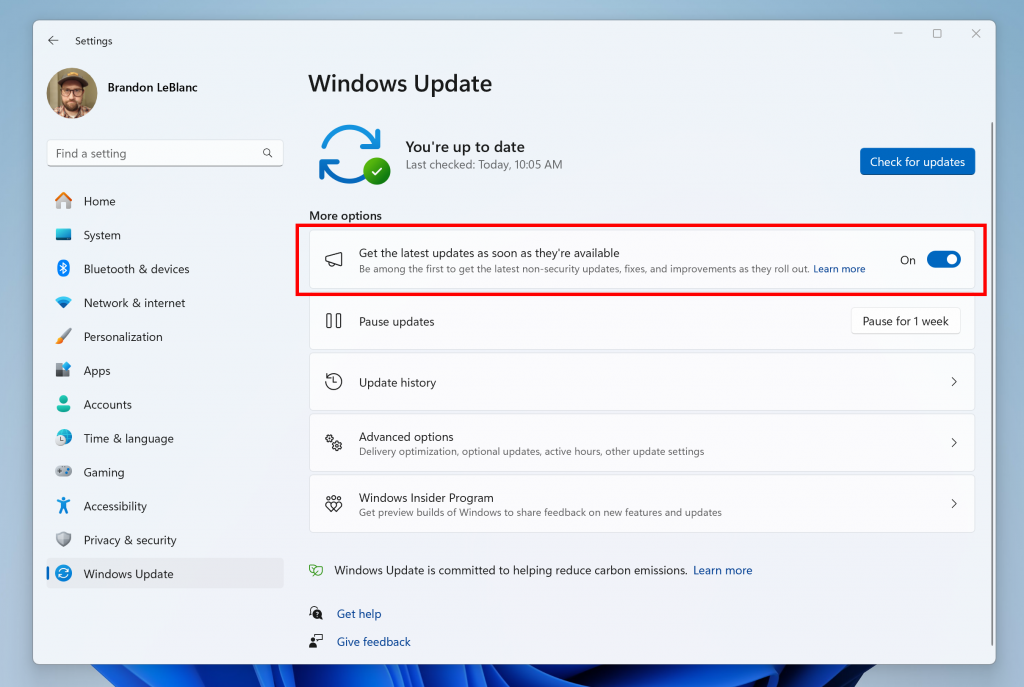
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.751 (KB5037874) to the Dev Channel. REMINDER: Windows Insiders in the Dev Channel will now receive updates based on Windows 11, version 24H2 via an enablement package (Build 26120.xxxx). For Insiders in the Dev Channel who want to be the first to get features […]
More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline following a destructive cyber attack staged by unidentified cyber actors, disrupting users’ access to the internet. The mysterious event, which took place between October 25 and 27, 2023, and impacted a single internet service provider (ISP) in the […]
Europol and German law enforcement have revealed the identities of eight cybercriminals linked to the various malware droppers and loaders disrupted as part of the Operation Endgame law enforcement operation. […]
A threat actor known as ShinyHunters is claiming to be selling a massive trove of Santander Bank data, including information for 30 million customers, employees, and bank account data, two weeks after the bank reported a data breach. […]
The post Here are just a few awesome examples of how AI is already transforming accessibility, as we partner broadly with developers, customers, and the disability community to use our platforms and tools to help create a more inclusive future for all. appeared first on Stories.
Microsoft has emphasized the need for securing internet-exposed operational technology (OT) devices following a spate of cyber attacks targeting such environments since late 2023. “These repeated attacks against OT devices emphasize the crucial need to improve the security posture of OT devices and prevent critical systems from becoming easy targets,” the Microsoft Threat Intelligence team […]