A suspected Chinese threat actor tracked as UNC3886 uses publicly available open-source rootkits named ‘Reptile’ and ‘Medusa’ to remain hidden on VMware ESXi virtual machines, allowing them to conduct credential theft, command execution, and lateral movement. […]
Author Archives: [email protected]
Hello Windows Insiders, today we’re releasing Windows 11 Build 26100.994 (KB5039304) to Insiders in the Release Preview Channel on Windows 11, version 24H2 (Build 26100). This update includes the following features and improvements: This update addresses an issue that affects Windows Defender Application Control (WDAC). It fails to verify the policies of some apps. […]
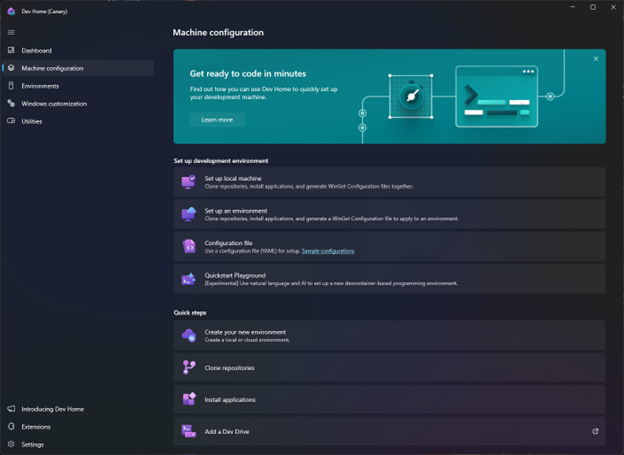
Welcome to the latest release of Dev Home, where we’ve been working to deliver your top asks. Dev Home is available by default and is open source on GitHub. Let’s dive into what‘s new! Machine configuration improvements The machine configuration tool is intended to help you get your developer machine set up in a snap. […]
Microsoft Edge is doubling down on our vision as the AI-powered, smarter browser. We keep innovating to make browsing more convenient, fast and fun. For us, AI is not just a trendy word. We are leading the way in using this magical technology for our customers’ benefit – with responsibility and customer trust at the […]
Threat actors are actively exploiting a SolarWinds Serv-U path-traversal vulnerability, leveraging publicly available proof-of-concept (PoC) exploits. […]
Car dealership SaaS platform CDK Global suffered an additional breach Wednesday night as it was starting to restore systems shut down in an previous cyberattack. […]
Cybersecurity researchers have disclosed details of a now-patched security flaw in Phoenix SecureCore UEFI firmware that affects multiple families of Intel Core desktop and mobile processors. Tracked as CVE-2024-0762 (CVSS score: 7.5), the “UEFIcanhazbufferoverflow” vulnerability has been described as a case of a buffer overflow stemming from the use of an unsafe variable in the […]
State-sponsored actors with ties to Russia have been linked to targeted cyber attacks aimed at French diplomatic entities, the country’s information security agency ANSSI said in an advisory. The attacks have been attributed to a cluster tracked by Microsoft under the name Midnight Blizzard (formerly Nobelium), which overlaps with activity tracked as APT29, BlueBravo, Cloaked […]
Originally published by Truyo.With the full text of the EU AI Act made public, Truyo President Dan Clarke read through the Act in its entirety to identify key elements that will be crucial to compliance for organizations in scope. The Act includes the conventional components of transparency, privacy, education, security, non-discrimination, and risk assessment.Where it […]
Originally published by Schellman&Co.If you’re a newly hired CISO or Director for an organization that’s required to achieve and maintain PCI DSS, you may be wondering how and where you can get started so that you’re ready when it comes time for the assessment to begin.No one wants to hear, “I’m putting you in charge […]