Learn more about how (and why) we created our Google AI Essentials course.
Author Archives: [email protected]
#WeArePlay celebrates Australian app and game founders of all sizes
Get ready to shop summer sales on Google with an updated deals destination, a new feature that compares membership pricing and more.
Google has developed a new framework called Project Naptime that it says enables a large language model (LLM) to carry out vulnerability research with an aim to improve automated discovery approaches. “The Naptime architecture is centered around the interaction between an AI agent and a target codebase,” Google Project Zero researchers Sergei Glazunov and Mark […]
CoinStats suffered a massive security breach that compromised 1,590 cryptocurrency wallets, with the attack suspected to have been carried out by North Korean threat actors. […]
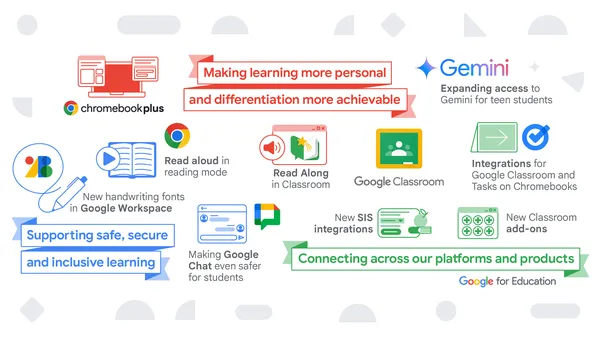
New features from Google for Education, including Gemini for teens and Chromebook Plus.
Google is responsibly bringing Gemini to teen students using their school accounts to help them learn confidently and empowering educators to enhance their impact with A…
Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial intelligence (AI) infrastructure platform that could be exploited to achieve remote code execution. Tracked as CVE-2024-37032, the vulnerability has been codenamed Probllama by cloud security firm Wiz. Following responsible disclosure on May 5, 2024, the issue was addressed in version
Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each story shines a light on underground activities, the threat actors involved, and why you should care, along with what you can do to mitigate risk. Cybersecurity professionals are facing unprecedented challenges as they strive to […]
Anthropic’s Claude 3.5 Sonnet, its latest, most capable model for now, has finally arrived on Amazon Bedrock. The post Claude 3.5 Sonnet launch on Bedrock doesn’t open AWS to OpenAI, Google models appeared first on MSPoweruser.