Multiple WordPress plugins have been backdoored to inject malicious code that makes it possible to create rogue administrator accounts with the aim of performing arbitrary actions. “The injected malware attempts to create a new administrative user account and then sends those details back to the attacker-controlled server,” Wordfence security researcher Chloe Chamberland said in a […]
Author Archives: [email protected]
Today the Acropolis Museum marks its 15th anniversary in collaboration with Google Arts & Culture.
CISA is warning that its Chemical Security Assessment Tool (CSAT) environment was breached in January after hackers deployed a webshell on its Ivanti device, potentially exposing sensitive security assessments and plans. […]
Google is testing a new feature called “Digital Credential API” for Chrome on Android that will allow websites to request identity information from mobile wallets using Android’s IdentityCredential system. […]
A novel command execution technique dubbed ‘GrimResource’ uses specially crafted MSC (Microsoft Saved Console) and an unpatched Windows XSS flaw to perform code execution via the Microsoft Management Console. […]
Four Vietnamese nationals linked to the international cybercrime group FIN9 have been indicted for their involvement in a series of computer intrusions that caused over $71 million in losses to companies in the U.S. […]
Learn more about how (and why) we created our Google AI Essentials course.
#WeArePlay celebrates Australian app and game founders of all sizes
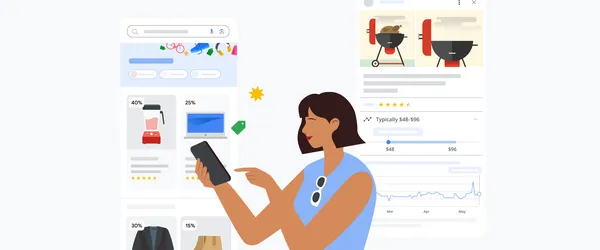
Get ready to shop summer sales on Google with an updated deals destination, a new feature that compares membership pricing and more.
Google has developed a new framework called Project Naptime that it says enables a large language model (LLM) to carry out vulnerability research with an aim to improve automated discovery approaches. “The Naptime architecture is centered around the interaction between an AI agent and a target codebase,” Google Project Zero researchers Sergei Glazunov and Mark […]