The Los Angeles Unified School District has confirmed a data breach after threat actors stole student and employee data by breaching the company’s Snowflake account. […]
Author Archives: [email protected]
The Treasury Department’s Office of Foreign Assets Control (OFAC) has sanctioned twelve Kaspersky Lab executives for operating in the technology sector of Russia. […]
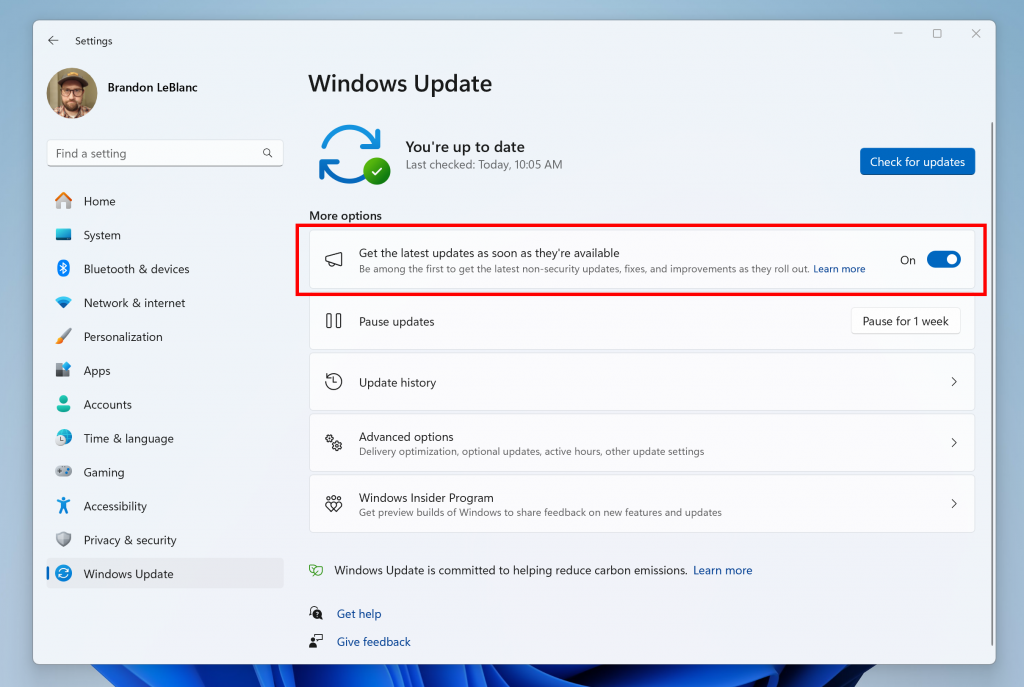
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 22635.3790 (KB5039307) to the Beta Channel. REMINDER: Windows Insiders in the Beta Channel will updates based on Windows 11, version 23H2 via an enablement package (Build 22635.xxxx). For Insiders in the Beta Channel who want to be the first to get features gradually rolled […]
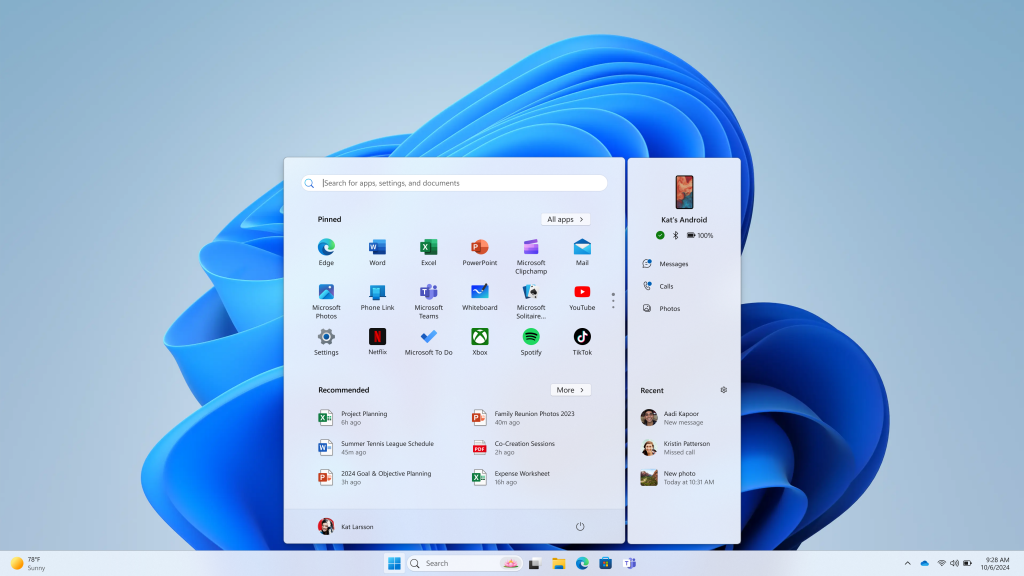
Hello Windows Insiders, We are gradually rolling out a new feature, which allows you to use your mobile device directly from the Start menu on your Windows 11 PCs, to Windows Insiders in the Beta Channel. With this feature, you can stay connected and effortlessly access your mobile device’s functionalities right from the Start menu. […]
UnitedHealth has confirmed for the first time what types of medical and patient data were stolen in the massive Change Healthcare ransomware attack, stating that data breach notifications will be mailed in July. […]
A federal jury in Las Vegas convicted five men for their involvement in the operation of Jetflicks, one of the largest and most popular illegal streaming services in the United States. […]
The Tor Project has released Tor Browser 13.5, bringing several improvements and enhancements for Android and desktop versions. […]
A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage campaign primarily targeting government entities across Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at least August 2023. “SneakyChef uses lures that are scanned documents of government agencies, most of which are related to various countries’ Ministries
Cybersecurity researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor. Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence. “While there are many methods used today to deploy malware, the […]
Does packing for holiday stress you out? Learn how to use Gemini to help you with your holiday preparation.