Google Translate adds 110 new languages using AI, breaking down communication barriers for millions around the world.
Author Archives: [email protected]
A critical security flaw has been disclosed in Fortra FileCatalyst Workflow that, if left unpatched, could allow an attacker to tamper with the application database. Tracked as CVE-2024-5276, the vulnerability carries a CVSS score of 9.8. It impacts FileCatalyst Workflow versions 5.1.6 Build 135 and earlier. It has been addressed in version 5.1.6 build 139. […]
Cyberespionage groups have been using ransomware as a tactic to make attack attribution more challenging, distract defenders, or for a financial reward as a secondary goal to data theft. […]
Recently-disrupted LockBit ransomware group, in what appears to be a desperate attempt to make a comeback, claimed this week that it had hit US Federal Reserve, the central bank of the United States. Except, the rumor has been quashed. […]
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published research looking into 172 key open-source projects and whether they are susceptible to memory flaws. […]
How Googlers used Gemini to build the Crossword puzzle, showing developers what’s possible with generative AI.
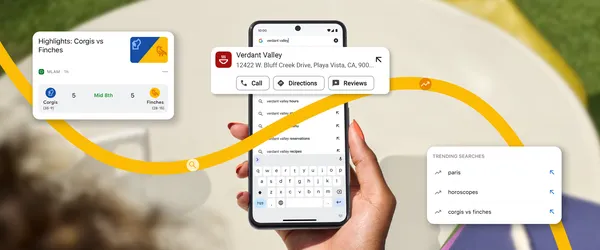
We’re making it easier to search in Chrome on iOS and Android with shortcut suggestions, live sports cards and more.
The Fortra FileCatalyst Workflow is vulnerable to an SQL injection vulnerability that could allow remote unauthenticated attackers to create rogue admin users and manipulate data on the application database. […]
New features in Google Analytics allow you to make better business decisions despite a continuously changing measurement landscape.
Testimony to the California Senate Judiciary Committee on June 25, 2024 by Jaffer Zaidi, Google VP of Global News Partnerships.