Fake IT support sites promote malicious PowerShell “fixes” for common Windows errors, like the 0x80070643 error, to infect devices with information-stealing malware. […]
Author Archives: [email protected]
Microsoft has resumed the rollout of the June Windows 11 KB5039302 update, now blocking the update only for those using virtualization software. […]
Hackers are exploiting a critical vulnerability that affects all D-Link DIR-859 WiFi routers to collect account information from the device, including passwords. […]
Google has announced that it’s going to start blocking websites that use certificates from Entrust starting around November 1, 2024, in its Chrome browser, citing compliance failures and the certificate authority’s inability to address security issues in a timely manner. “Over the past several years, publicly disclosed incident reports highlighted a pattern of concerning behaviors […]
The new Brain Cipher ransomware operation has begun targeting organizations worldwide, gaining media attention for a recent attack on Indonesia’s temporary National Data Center. […]
Infosys McCamish Systems (IMS) disclosed that the LockBit ransomware attack it suffered earlier this year impacted sensitive information of more than six million individuals. […]
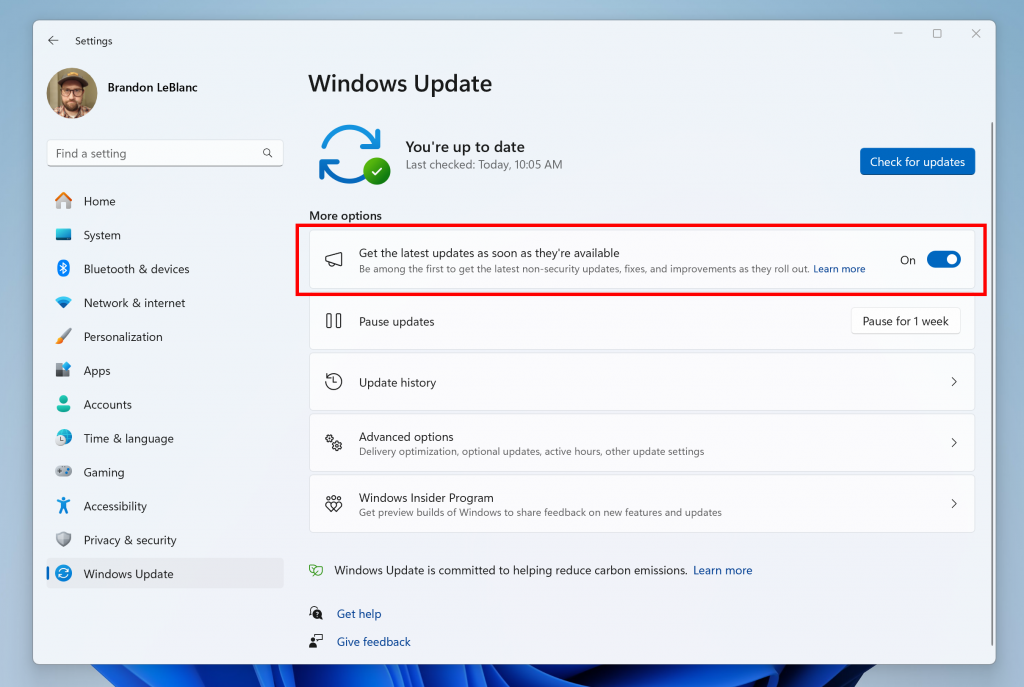
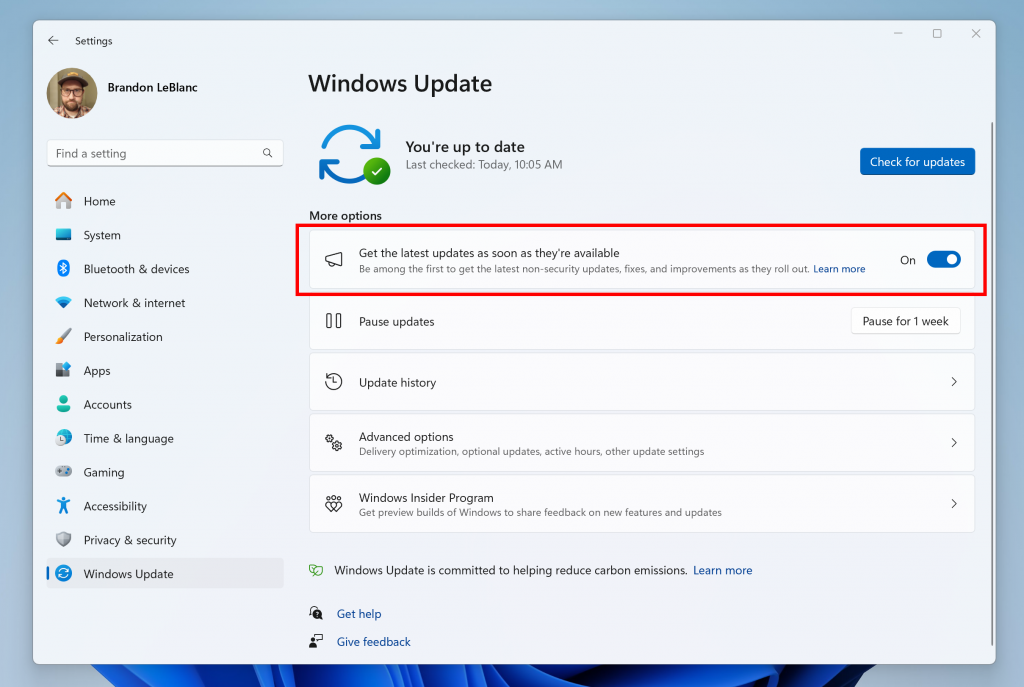
Hello Windows Insiders, we are beginning to enable the following new features, changes and improvements, and fixes to the Dev Channel for Insiders on Build 26120.961 who have turned ON the toggle (shown in the image below) to get the latest updates as they are available via Settings > Windows Update. We’re starting the enablement […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26244 to the Canary Channel. Developers, please note that for a short period of time, we will not be releasing an SDK for builds we flight to the Canary Channel. Changes and Improvements [General] This update includes a small set of general improvements […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 22635.3858 (KB5039327) to the Beta Channel. REMINDER: Windows Insiders in the Beta Channel will updates based on Windows 11, version 23H2 via an enablement package (Build 22635.xxxx). For Insiders in the Beta Channel who want to be the first to get features gradually rolled […]
Agropur, one of the largest dairy cooperatives in North America, is notifying customers of a data breach after some of its shared online directories were exposed. […]