CISA and the FBI urged software companies on Wednesday to review their products and eliminate path OS command injection vulnerabilities before shipping. […]
Author Archives: [email protected]
Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) is warning that Japanese organizations are being targeted in attacks by the North Korean ‘Kimsuky’ threat actors. […]
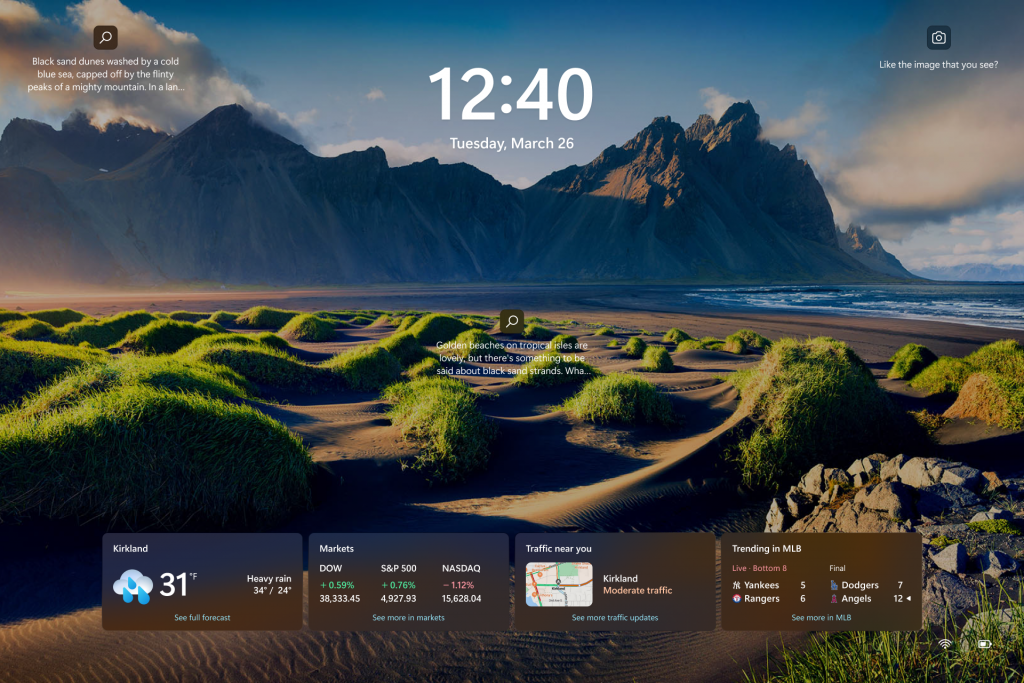
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26252 to the Canary Channel. Developers, please note that for a short period of time, we will not be releasing an SDK for builds we flight to the Canary Channel. Changes and Improvements [Lock screen] We’re beginning to roll out Weather and more to […]
7-zip, Advanced IP Scanner, AIMP, AnyDesk, AutoDesk, Bastion Secure, Bitwarden, Blackberry, Combi Security, eSentire, Fin7, Krebs, Malwarebytes, Microsoft, Ne'er-Do-Well News, News, Node.js, Notepad, pgAdmin, ProDaft, ProtectedPDFViewer, PuTTY, Python, ransomware, Rest Proxy, Russia's War on Ukraine, Security, Silent Push, spearphishing, Stark Industries Solutions, Sublime Text, typosquatting, Web Fraud 2.0, Zach Edwards
The Stark Truth Behind the Resurgence of Russia’s Fin7
The Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion in losses since 2013, was declared dead last year by U.S. authorities. But experts say Fin7 has roared back to life in 2024 — setting up thousands of websites mimicking a range of media […]
Microsoft fixed a Windows zero-day vulnerability that has been actively exploited in attacks for eighteen months to launch malicious scripts while bypassing built-in security features. […]
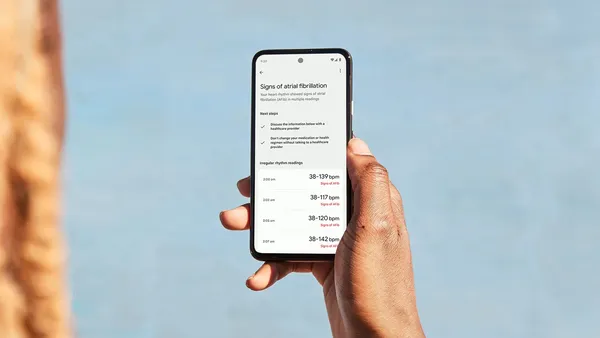
Fitbit’s Irregular Rhythm Notification feature is now available via Web API to healthcare providers with user permission.
Microsoft has fixed a known issue causing restart loops and taskbar problems on Windows 11 systems after installing the June KB5039302 preview update. […]
Microsoft is reportedly leaving its observer seat on the OpenAI board, followed by Apple, amidst antitrust scrutiny. The post Microsoft, OpenAI’s main financial backer, drops its board observer position appeared first on MSPoweruser.
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. Singapore-headquartered Group-IB, which discovered the threat actor in early April 2024, said the modus operandi involved the exploitation of CVE-2023-27532 (CVSS score: 7.5) to carry out the malicious activities. Initial access to the target
Microsoft finally patches a month-old issue of the taskbar not showing up after Windows 11’s Patch Tuesday update from June 2024. The post Microsoft fixes issue with taskbar not showing after Windows 11’s KB5039302 June update appeared first on MSPoweruser.