SonicWall has released patches to address three security flaws affecting SMA 100 Secure Mobile Access (SMA) appliances that could be fashioned to result in remote code execution. The vulnerabilities are listed below – CVE-2025-32819 (CVSS score: 8.8) – A vulnerability in SMA100 allows a remote authenticated attacker with SSL-VPN user privileges to bypass the path […]
Author Archives: [email protected]
Threat actors with ties to the Qilin ransomware family have leveraged malware known as SmokeLoader along with a previously undocumented .NET compiled loader codenamed NETXLOADER as part of a campaign observed in November 2024. “NETXLOADER is a new .NET-based loader that plays a critical role in cyber attacks,” Trend Micro researchers Jacob Santos, Raymart Yambot, […]
Since the start of the year, the Russian state-backed ColdRiver hacking group has been using new LostKeys malware to steal files in espionage attacks targeting Western governments, journalists, think tanks, and non-governmental organizations. […]
Originally published by VikingCloud. Small and medium-sized businesses (SMBs) play a crucial role in the U.S. economy, making up 99.9% of all businesses and contributing to half of the nation’s GDP. However, these vital economic growth drivers face an escalating threat —cyberattacks that could put them out of business. Nearly 1 in 5 SMBs […]
Building on Google’s ongoing carbon removal efforts, we’re announcing two new partnerships to help our atmosphere in the near-term by eliminating superpollutants. Our pa…
SonicWall has urged its customers to patch three security vulnerabilities affecting its Secure Mobile Access (SMA) appliances, one of them tagged as exploited in attacks […]
61% of security leaders reported suffering a breach due to failed or misconfigured controls over the past 12 months. This is despite having an average of 43 cybersecurity tools in place. This massive rate of security failure is clearly not a security investment problem. It is a configuration problem. Organizations are beginning to understand that […]
The nation-state threat actor known as MirrorFace has been observed deploying malware dubbed ROAMINGMOUSE as part of a cyber espionage campaign directed against government agencies and public institutions in Japan and Taiwan. The activity, detected by Trend Micro in March 2025, involved the use of spear-phishing lures to deliver an updated version of a backdoor […]
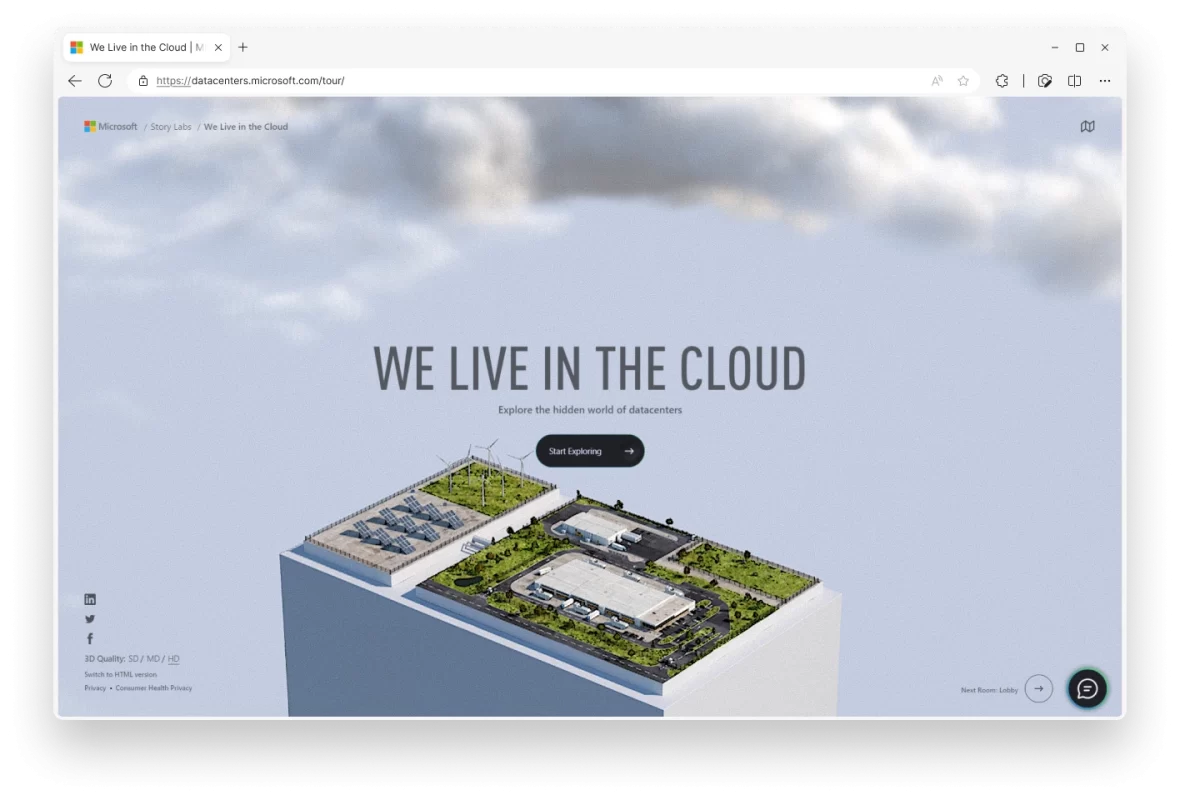
Imagine stepping into a realm where the cloud meets cutting-edge technology, revealing the inner workings behind servers, fiber optic network cables, operations, physical datacenter buildings, and the most advanced AI infrastructure. This is Microsoft’s Virtual Datacenter Tour, where customers can explore the infrastructure and datacenter design that powers over 60 datacenter regions and 300 plus […]
Over the past year, we’ve seen AI agents evolve from experimental tools to essential components of enterprise systems. From simple prompt and response bots to agents that act autonomously on your behalf, this shift marks a new era of software design where intelligence is no longer tied to static interfaces or single applications. At Microsoft, […]