With the recent release of Copilot+ PCs, developers are increasingly focused on optimizing their apps for these devices. Copilot+ PCs are the fastest, most intelligent Windows PCs ever built. With powerful new system architecture designed to deliver best-in-class performance, all–day battery life and the ability to run the most advanced AI models on device, Copilot+ […]
Author Archives: [email protected]
The Australian Human Rights Commission (AHRC) disclosed a data breach incident where private documents leaked online and were indexed by major search engines. […]
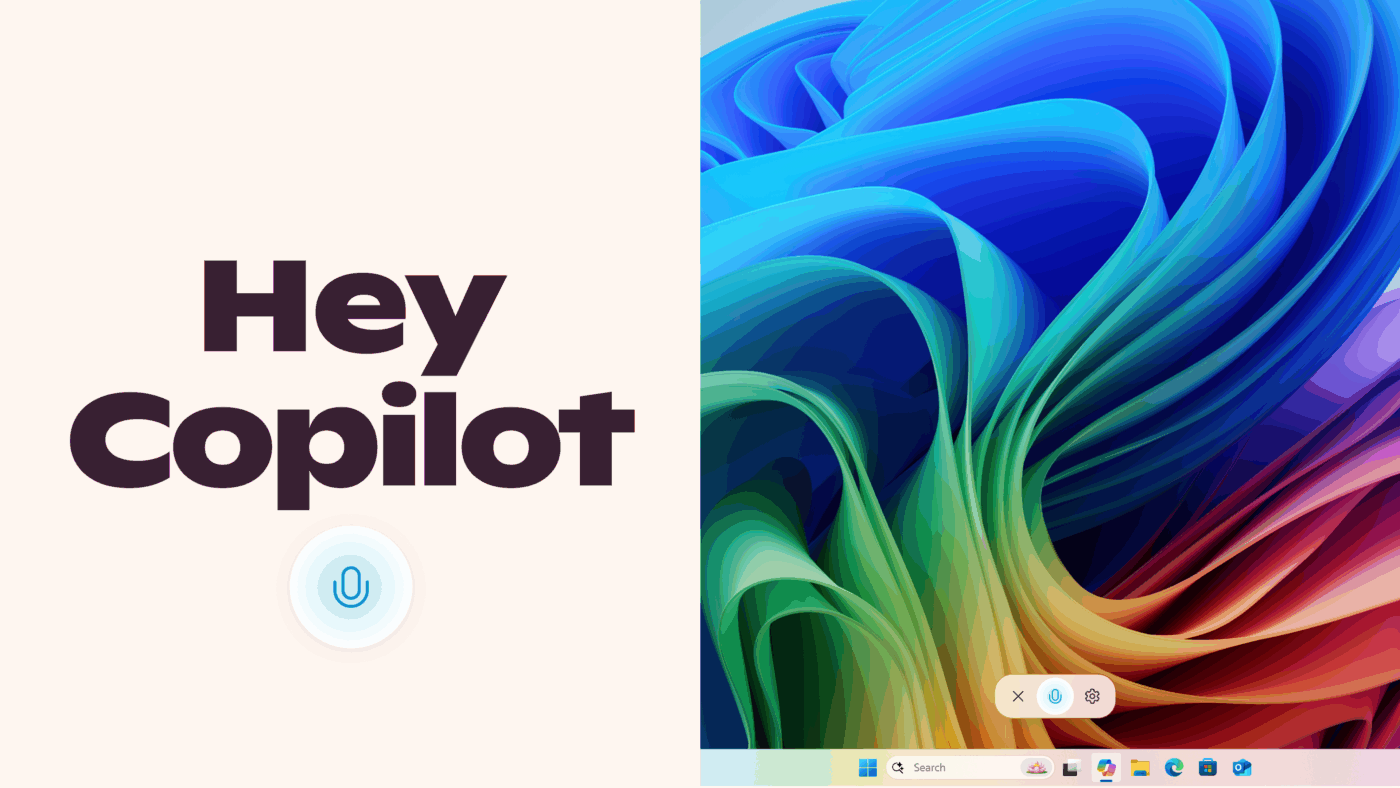
Hello Windows Insiders, we are beginning to roll out an update for the Microsoft Copilot app on Windows via the Microsoft Store which introduces the following changes and improvements: Copilot wake word: Windows Insiders can now invoke Copilot with the phrase “Hey, Copilot!”. This opt-in feature gives people a new way to easily start a […]
Device Trust from Android Enterprise helps enable secure access to work data on any Android device by verifying trust signals.
A Chinese-language, Telegram-based marketplace called Xinbi Guarantee has facilitated no less than $8.4 billion in transactions since 2022, making it the second major black market to be exposed after HuiOne Guarantee. According to a report published by blockchain analytics firm Elliptic, merchants on the marketplace have been found to peddle technology, personal data, and money […]
Today, Google Cloud announced a first-of-its-kind Generative AI Leader certification program. It’s specifically designed for non-technical professionals like managers, s…
Microsoft has fixed a known issue preventing Linux from booting on dual-boot systems with Secure Boot enabled after installing the August 2024 Windows security updates. […]
A cybersecurity incident on Nucor Corporation’s systems forced the company to take offline parts of its networks and implement containment measures. […]
A new global phishing threat called “Meta Mirage” has been uncovered, targeting businesses using Meta’s Business Suite. This campaign specifically aims at hijacking high-value accounts, including those managing advertising and official brand pages. Cybersecurity researchers at CTM360 revealed that attackers behind Meta Mirage impersonate official Meta communications, tricking users into handing
New phishing tactics are abusing trusted domains, real CAPTCHAs, and server-side email validation to selectively target victims with customized fake login pages. Keep Aware’s latest research breaks down the full attack chain and how these zero-day phish operate. […]