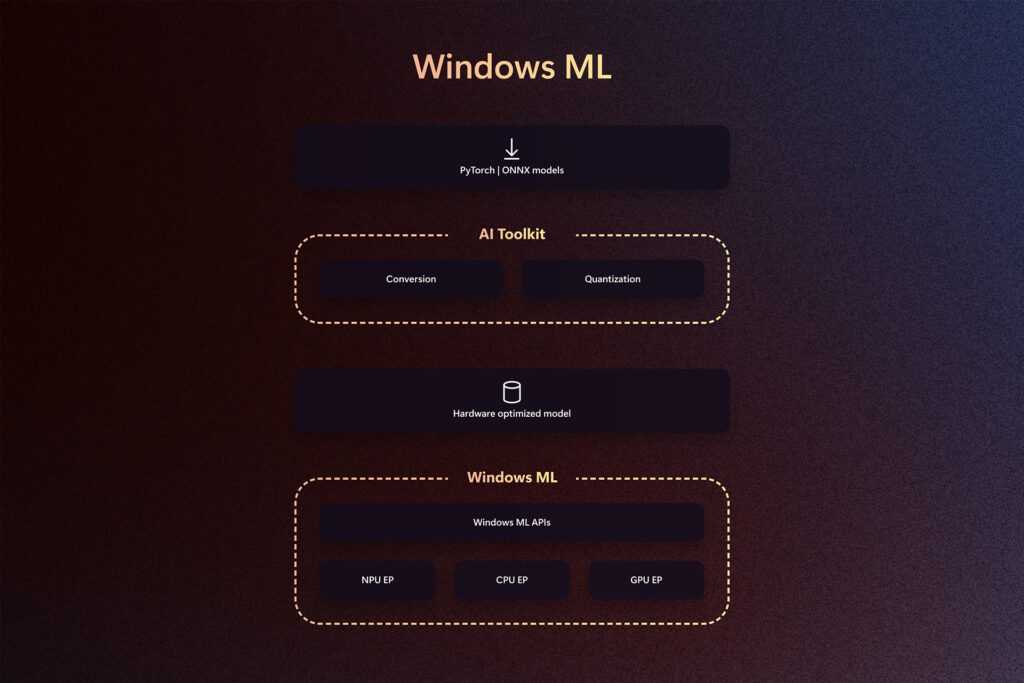
Machine learning is at the forefront of technological innovation, enabling transformative user experiences. With the advances in client silicon and model miniaturization, new scenarios are feasible to run completely locally. To support developers shipping production experiences in the increasingly complex AI landscape, we are thrilled to announce the public preview of Windows ML – a cutting-edge runtime […]
Author Archives: [email protected]
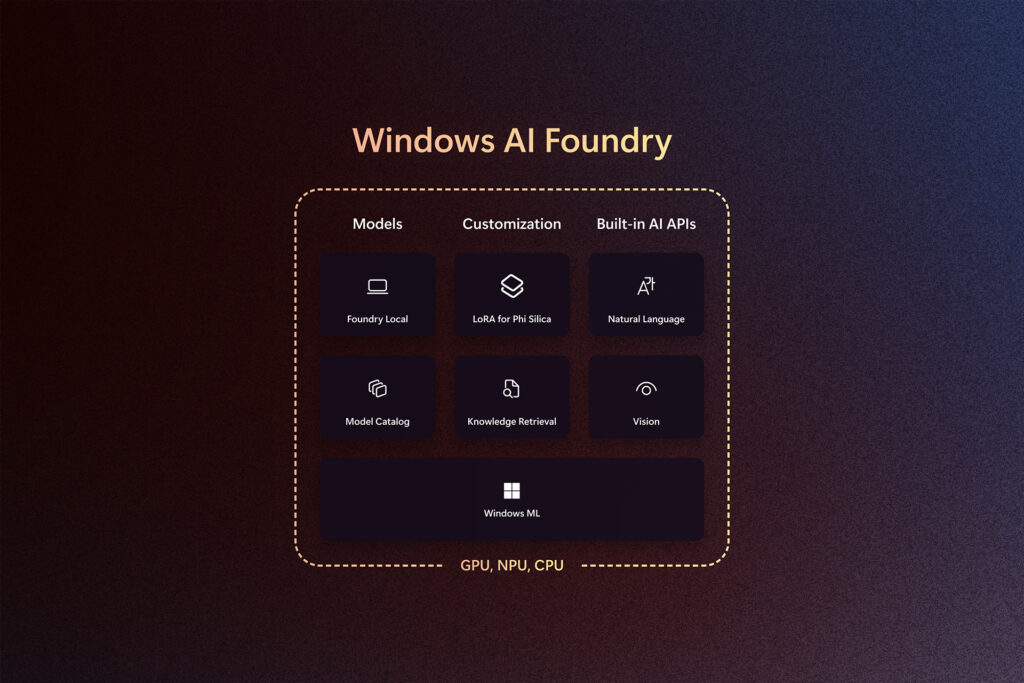
Today, we announced powerful capabilities for AI development with Windows AI Foundry, featuring components like Windows ML that enable developers to bring their own models and deploy them efficiently across diverse silicon partner ecosystem including – AMD, Intel, NVIDIA and Qualcomm spanning CPU, GPU, NPU (Neural Processing Unit). In the rapidly evolving field of AI […]
The Windows developer platform continues to evolve, bringing more quality, performance and innovation through Copilot+ PC. This translates into a tremendous opportunity for app developers that are looking to scale their user acquisition strategies, to deepen engagement, to invent on larger form factors where immersive experiences thrive. It’s been exciting to witness the momentum and […]
We’re excited to be back at Build, a special moment each year to connect with the global developer community. It’s energizing to share what we’ve been working on, and just as important, to hear how developers are using Microsoft platforms to build what’s next. At Microsoft, we believe the future of AI is being built […]
Microsoft has open-sourced the Windows Subsystem for Linux (WSL), making its source code available on GitHub, except for a few components that are part of Windows. […]
The official site for RVTools has been hacked to serve a compromised installer for the popular VMware environment reporting utility. “Robware.net and RVTools.com are currently offline. We are working expeditiously to restore service and appreciate your patience,” the company said in a statement posted on its website. “Robware.net and RVTools.com are the only authorized and […]
The United Kingdom’s Legal Aid Agency (LAA) has confirmed that a recent cyberattack is more serious than first believed, with hackers stealing a large trove of sensitive applicant data in a data breach. […]
Several ransomware actors are using a malware called Skitnet as part of their post-exploitation efforts to steal sensitive data and establish remote control over compromised hosts. “Skitnet has been sold on underground forums like RAMP since April 2024,” Swiss cybersecurity company PRODAFT told The Hacker News. “However, since early 2025, we have observed multiple ransomware […]
Mozilla released emergency security updates to address two Firefox zero-day vulnerabilities demonstrated in the recent Pwn2Own Berlin 2025 hacking competition. […]
The Pwn2Own Berlin 2025 hacking competition has concluded, with security researchers earning $1,078,750 after exploiting 29 zero-day vulnerabilities and encountering some bug collisions. […]