A flaw in O2 UK’s implementation of VoLTE and WiFi Calling technologies could allow anyone to expose the general location of a person and other identifiers by calling the target. […]
Author Archives: [email protected]
Microsoft has released out-of-band updates to fix a known issue causing Windows 10 systems to boot into BitLocker recovery after installing the May 2025 security updates. […]
Arla Foods has confirmed to BleepingComputer that it was targeted by a cyberattack that has disrupted its production operations. […]
Hello Windows Insiders, today we’re releasing Windows 11 Build 26100.4188 (KB5058499) to Insiders in the Release Preview Channel on Windows 11, version 24H2 (Build 26100). Below is a summary of the new features and improvements included as part of this update separated into two sections: gradual rollout and normal rollout. The bold text within the […]
Microsoft is replacing ‘Copilot Runtime’ with Windows AI Foundry to help developers build, experiment, and reach users with AI experiences in their apps. […]
At the Build 2025 developer conference, Microsoft announced a new ‘Advanced Settings’ feature to help users and developers personalize the OS experience. […]
Welcome to Build 2025! Today, we are thrilled to connect with our incredible developer community and share some exciting announcements for developing with AI. As an AI-powered browser, Microsoft Edge aims to make it easier for developers to offer AI functionality, and for everyone to make the most out of AI. There are also exciting […]
As AI agents become more capable and integrated into daily workflows, the need for secure, standardized communication between tools and agents has never been greater. At Microsoft Build 2025, we’re announcing an early preview of how Windows 11 is embracing the Model Context Protocol (MCP) as a foundational layer for secure, interoperable agentic computing — […]
Today we’re very excited to announce the open-source release of the Windows Subsystem for Linux. This is the result of a multiyear effort to prepare for this, and a great closure to the first ever issue raised on the Microsoft/WSL repo: Will this be Open Source? · Issue #1 · microsoft/WSL. That means that the […]
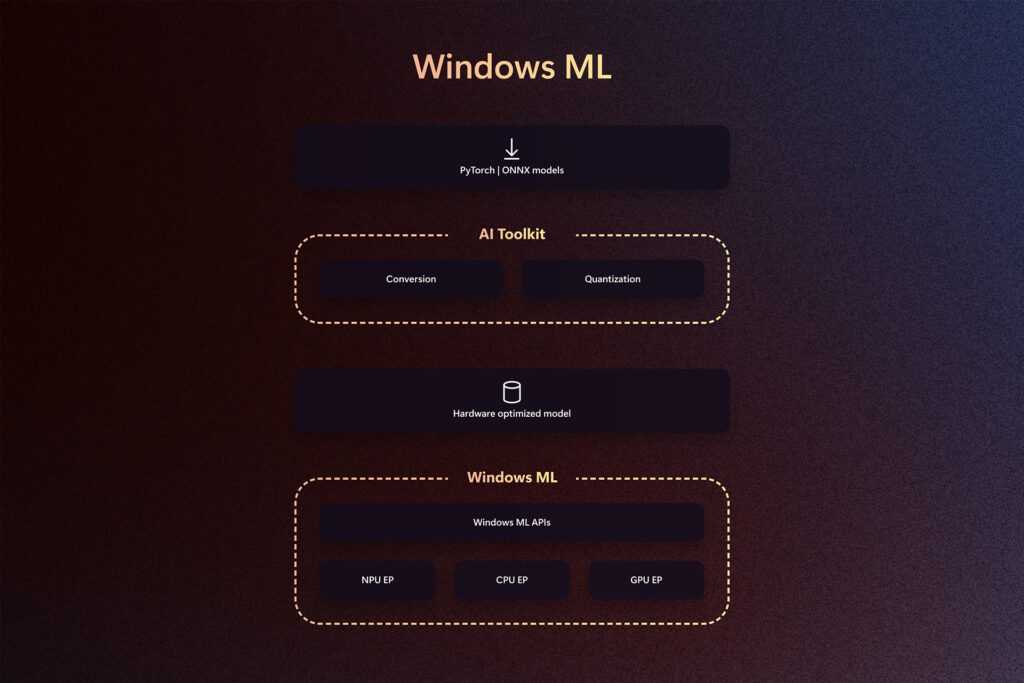
Machine learning is at the forefront of technological innovation, enabling transformative user experiences. With the advances in client silicon and model miniaturization, new scenarios are feasible to run completely locally. To support developers shipping production experiences in the increasingly complex AI landscape, we are thrilled to announce the public preview of Windows ML – a cutting-edge runtime […]