The US Cybersecurity and Infrastructure Security Agency (CISA) is warning that Contec CMS8000 devices, a widely used healthcare patient monitoring device, include a backdoor that quietly sends patient data to a remote IP address and downloads and executes files on the device. […]
Author Archives: [email protected]
The Gemini app is now using Gemini 2.0 Flash. This model delivers fast responses and stronger performance across a number of key benchmarks, providing everyday help with…
Google blocked 2.3 million Android app submissions to the Play Store in 2024 due to violations of its policies that made them potentially risky for users. […]
The New York Blood Center (NYBC), one of the world’s largest independent blood collection and distribution organizations, says a Sunday ransomware attack forced it to reschedule some appointments. […]
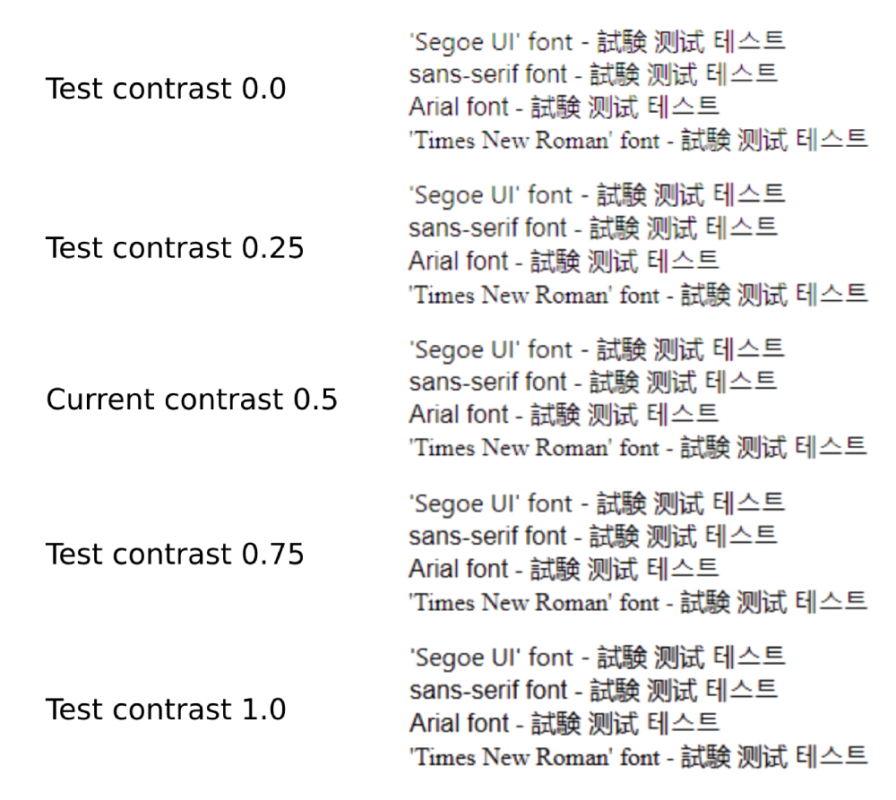
In today’s digital age, browser users spend significant time reading content online. The contrast ratio between the text and its background is therefore very important to ensure comfort and to reduce eye strain. That’s why, based on your feedback, we had already enhanced text rendering in Microsoft Edge back in 2021. Today, we’re taking things […]
A Little Sunshine, ACB Group, Amazon AWS, Anjie CDN, Crowell & Moring LLP, Fangneng CDN, Funnull, infrastructure laundering, Krebs, Microsoft Azure, Ne'er-Do-Well News, NETSCOUT, News, NoName057(16), polyfill, Richard Hummel, Security, Silent Push, Suncity Group, Time to Patch, U.S. Department of Commerce, Web Fraud 2.0, Zach Edwards
Infrastructure Laundering: Blending in with the Cloud
Image: Shutterstock, ArtHead. In an effort to blend in and make their malicious traffic tougher to block, hosting firms catering to cybercriminals in China and Russia increasingly are funneling their operations through major U.S. cloud providers. Research published this week on one such outfit — a sprawling network tied to Chinese organized crime gangs and […]
At the big game, Google will demonstrate how our products and technologies help individuals and businesses.
In Avowed, the immersive fantasy role-playing game from Obsidian launching on Feb. 18, players have more freedom than ever before in quests, character interactions and combat. Xbox Wire’s Mike Nelson spoke with the team behind the title to explore the philosophy behind that level of agency. “Everywhere I looked was an opportunity to engage with […]
Over 57 distinct threat actors with ties to China, Iran, North Korea, and Russia have been observed using artificial intelligence (AI) technology powered by Google to further enable their malicious cyber and information operations. “Threat actors are experimenting with Gemini to enable their operations, finding productivity gains but not yet developing novel capabilities,” Google Threat
DeepSeek, the Chinese AI startup known for its DeepSeek-R1 LLM model, has publicly exposed two databases containing sensitive user and operational information. […]