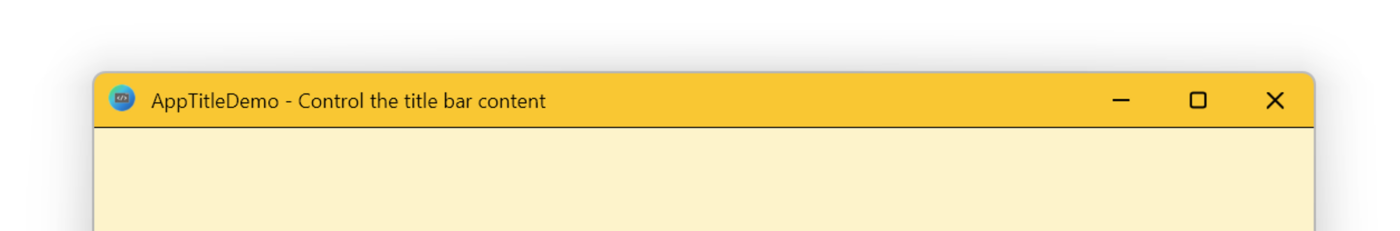
Starting with Microsoft Edge 134 (and Chrome 134), we’re happy to announce the availability of a new HTML meta tag, <meta name=”application-title”>, which allows developers to control the text that appears in the title bar of their installed applications. When developing a web application, giving your users a good experience is important. Across the various […]
Author Archives: [email protected]
The US Cybersecurity & Infrastructure Security Agency (CISA) has added four vulnerabilities to its Known Exploited Vulnerabilities catalog, urging federal agencies and large organizations to apply the available security updates as soon as possible. […]
CSA’s Cloud Controls Matrix (CCM) is a security framework for cloud computing. It contains 197 control objectives structured into 17 domains. These domains cover all key aspects of cloud technology.You can use CCM to systematically assess a cloud implementation. CCM also provides guidance on which actors within the cloud supply chain should implement which controls.CCM […]
Since December’s launch of Gemini 2.0 Flash Experimental, our developer community has been exploring its capabilities, and the results are impressive. Companies lik…
Starting today, Gemini app users can try 2.0 Flash Thinking Experimental. It’s currently ranked as the world’s best model, and it’s available at no cost. Built on the sp…
We’re announcing new updates to Gemini 2.0 Flash, plus introducing Gemini 2.0 Flash-Lite and Gemini 2.0 Pro Experimental.
The Spanish police have arrested a suspected hacker in Alicante for allegedly conducting 40 cyberattacks targeting critical public and private organizations, including the Guardia Civil, the Ministry of Defense, NATO, the US Army, and various universities. […]
AWS S3 bucket names are global with predictable names that can be exploited in “S3 bucket namesquatting” attacks to access or hijack S3 buckets. In this article, Varonis explains how these attacks work and how you can prevent them. […]
The North Korea-linked Lazarus Group has been linked to an active campaign that leverages fake LinkedIn job offers in the cryptocurrency and travel sectors to deliver malware capable of infecting Windows, macOS, and Linux operating systems. According to cybersecurity company Bitdefender, the scam begins with a message sent on a professional social media network, enticing […]
Cybercriminals are increasingly leveraging legitimate HTTP client tools to facilitate account takeover (ATO) attacks on Microsoft 365 environments. Enterprise security company Proofpoint said it observed campaigns using HTTP clients Axios and Node Fetch to send HTTP requests and receive HTTP responses from web servers with the goal of conducting ATO attacks. “Originally sourced from public